Table of Contents
Overview
With Azure AD’s certificate-based authentication (CBA) there is a way to get a Primary Refresh Token (PRT) inside the User’s Citrix Session. I’ve written about the details in Part1.
As the most negative requirement is to deploy User-Certificates to the Endpoints (difficult in a BYOD-scenario) – I’ve decided to work on another way to achieve SSO inside the Citrix Session for subsequent Applications, without a PRT. The goal is to have no additional user-interaction. That’s the content of this post, Part2.
The Login Process
Because of the default SAML / OAuth Loginflow with FAS, there is already a Smartcard certificate enrolled and used for the SSO to the VDA – why don’t make usage of this for other process? I will use the in-session certificate for auto-select Azure AD CBA SSO to M365 Apps – without any PRT.
Configuration
A configured and enabled Azure AD CBA authentication method, like described in Part1, is the basic requirement. There is no obligatory need for Azure AD Hybrid Join (HAADJ) of the Clients or the VDA, otherwise there are many other benefit for doing HAADJ.
FAS
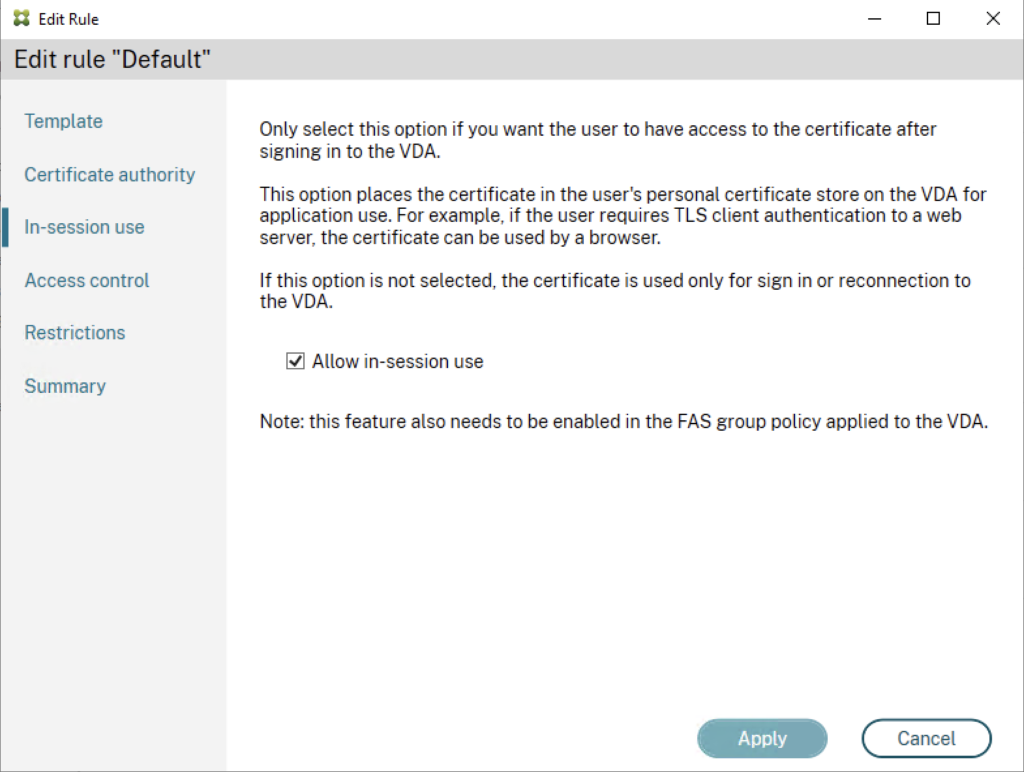
Edit the default or your created Rule inside the FAS Console and enable in-session use:
GPO VDA FAS
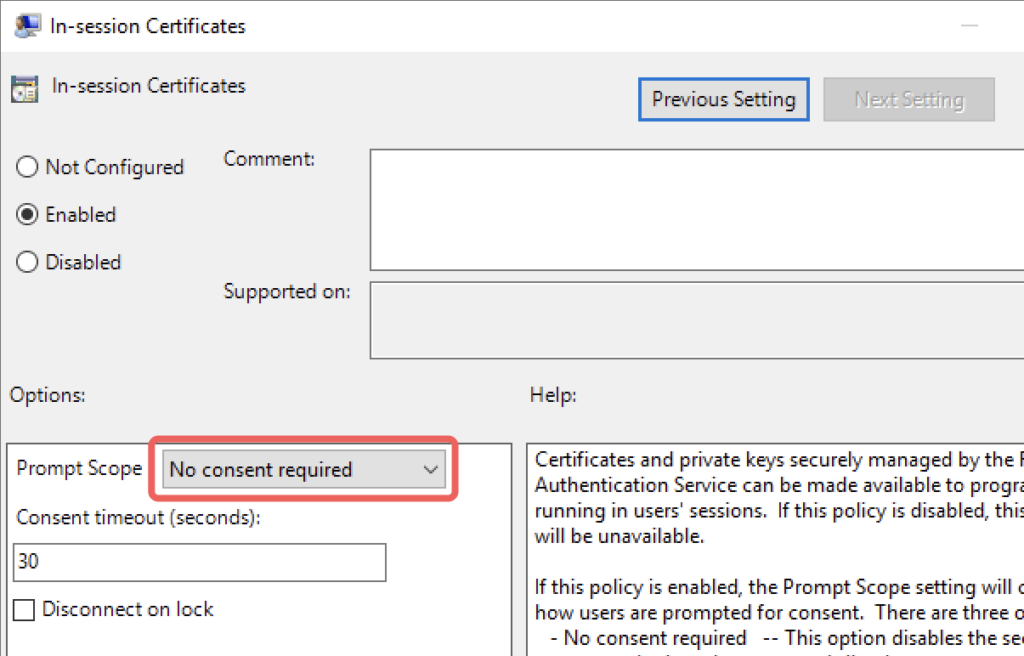
Edit your FAS GPO, linked to your VDAs and enable In-session Certificates with a Prompt Scope of No consent required. The timeout will be ignored but the field can’t be empty, so insert for example 30 seconds.
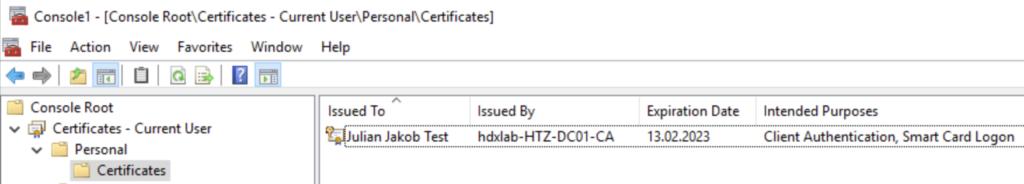
You can check if the Certificate is visible to the user in a Citrix Session:
GPO VDA Edge
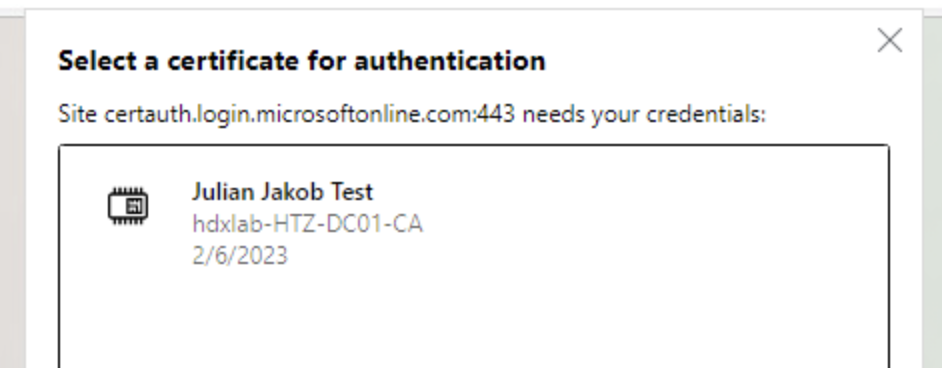
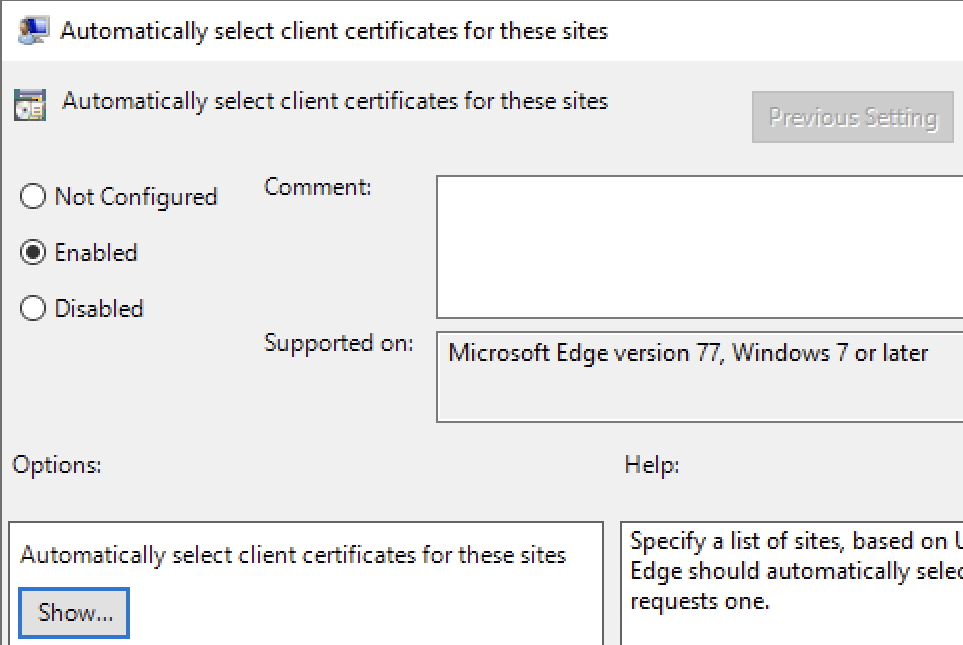
Configure the following GPO on your VDAs, so there will be no certificate prompt and Microsoft Edge (which is my default browser, so it’s used by all kind of M365 Apps for doing their authentication stuff) is silently signing in. Otherwise you’re getting the following popup and the User will not understand what to do 🙂
Location:
Administrative Templates / Microsoft Edge / Content settings
Parameter:
Automatically select client certificates for these sites
Value (Replace hdxlab-HTZ-DC01-CA with the Common Name (CN) of your CA):
{“pattern”:”https://certauth.login.microsoftonline.com”,”filter”:{“ISSUER”:{“CN”:”hdxlab-HTZ-DC01-CA”}}}
PKI
If you followed the FAS Instructions from CTP Julian Mooren, you may have deleted the Client Authentication extension within the Citrix_SmartcardLogon certificate template. Double check if it’s included, otherwise you have to add the extension so it looks like this:
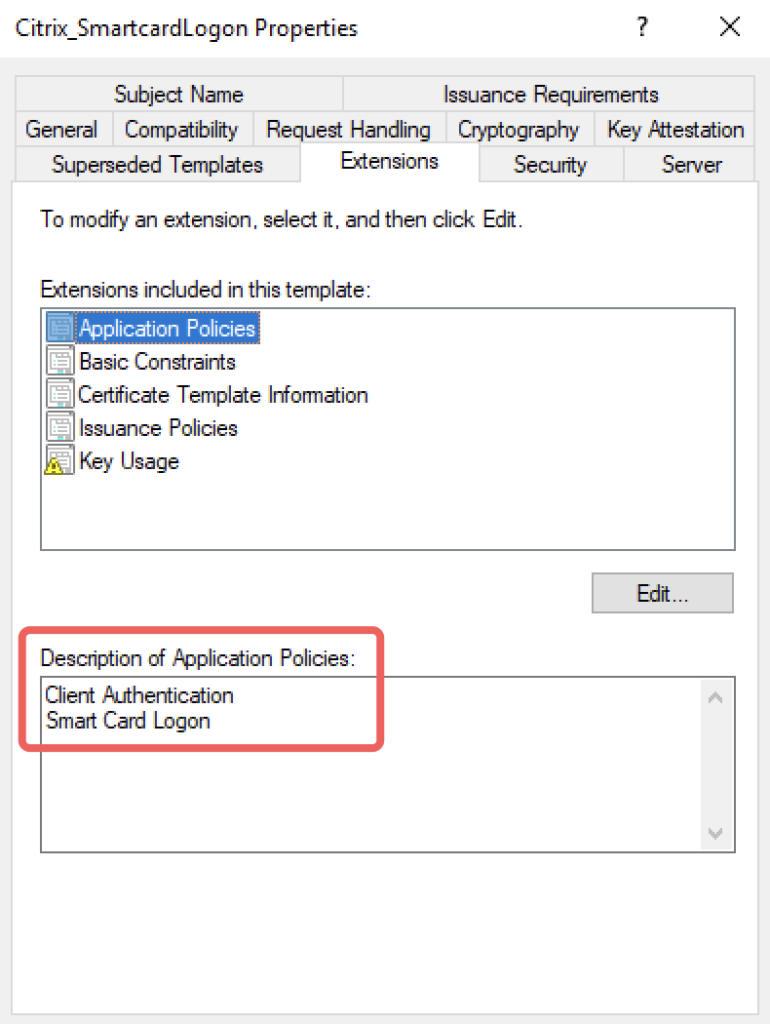
There you go. Apps like Office, Teams, MS Edge or OneDrive will silently sign-in with the User’s Citrix_SmartcardLogon certificate, available within the Citrix Session.
Summary
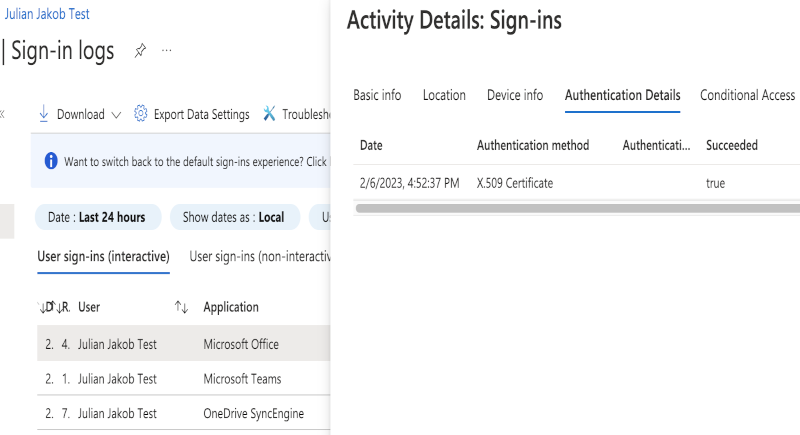
Here is the Azure AD Sign-in log for my Testuser, you can see a successful X.509 Certificate authentication for the Office, Teams and OneDrive Applications:
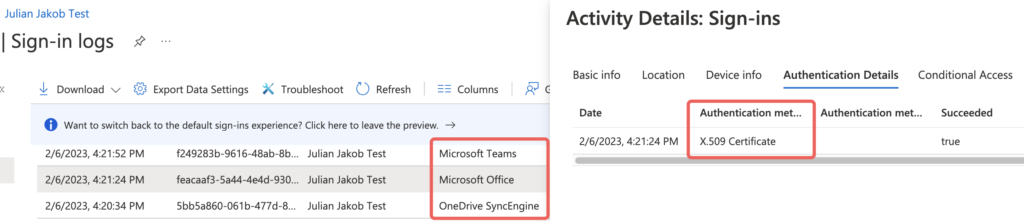
I hope this post provides another opportunity for the Users’ familiar SSO experience when dealing with FAS setups.
Hints
Make sure your Conditional Access policies are configured correctly for internal certificate-based authentication. Otherwise you’re getting a MFA prompt after the CBA auto sign-in.
Hi Julian – awesome article – congrats!
However – I do have an issue with the pattern for the Edge Policy. Maybe you have an idea what I did wrong.
My about:policy in Edge says the following:
Error: “Error at AutoSelectCertificateForUrls[0]: Error while parsing JSON value: Line: 1, column: 2, Dictionary keys must be quoted.”
I’ve entered following line to the policy:
{“pattern”:”https://certauth.login.microsoftonline.com”,”filter”:{“ISSUER”:{“CN”:”MYCA”}}}
any help would be highly appreciated.
Thanks for your work
Christoph
Hi Christoph,
thank you! Is it a copy-paste issue with the quotation marks? Try copy this one:
{“pattern”:”https://certauth.login.microsoftonline.com”,”filter”:{“ISSUER”:{“CN”:”MYCA”}}}
Regards
Julian
Hi Julian,
yes – you’re right. The quotation marks were incorrect.
Apologizes for not better checking myself.
In the meantime we’ve managed to get it working 🙂
Including PRT and X.509 Certificate authentication.
I suppose that this will save us ~250 Support Tickets a year.
Thanks again for your awesome work!!!!
br
Christoph
Hi Julian,
Great article! In our environment we have 2 different CAs that could issue the FAS certificate. How would I specify both CN certificate issuer names in the Edge GPO?
Would love to know the same!
Yeah, just add 2 rules, one for each issuer.