Table of Contents
Overview
There are several discussions about the missing Primary Refresh Token (PRT) in the User’s Citrix Session when using SAML / oAuth with Azure AD and Citrix FAS – as using Smartcard to authenticate is missing the User’s credentials, so there’s no way to issue a PRT.
What is a Primary Refresh Token?
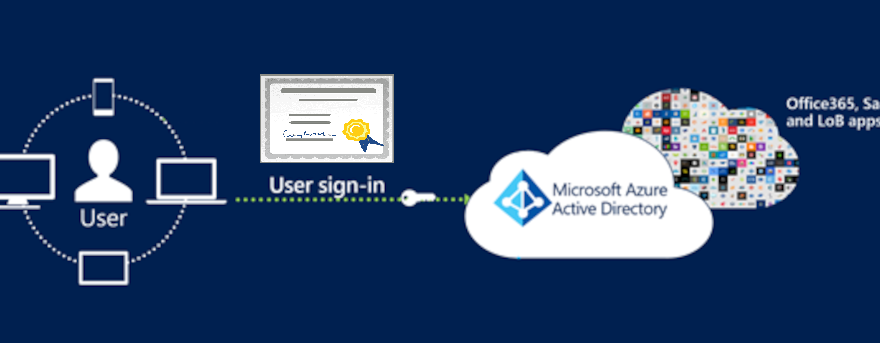
A Primary Refresh Token (PRT) is a key artifact of Azure AD authentication on Windows 10 or newer, Windows Server 2016 and later versions, iOS, and Android devices. It is a JSON Web Token (JWT) specially issued to Microsoft first party token brokers to enable single sign-on (SSO) across the applications used on those devices.
Microsoft recommends using the latest versions of Windows 10, Windows 11 and Windows Server 2019+ to get the best SSO experience.
So, missing SSO to Microsoft / 365 / Enterprise Applications is the consequence when using Azure AD as IdP with Citrix FAS.
So what’s new here with this post? There’s one important note in Azure AD’s certificate-based authentication documentation “Users will get a primary refresh token (PRT) from Azure Active Directory after the successful login and depending on the Certificate-based authentication configuration, the PRT will contain the multifactor claim.” Also, it eliminates the need for federated ADFS and reduces the cost and on-premises footprint. It’s a free feature, and you don’t need any paid editions of Azure AD to use it.
And that’s what I’m talking about in this post. Gain SSO into all further Applications with a PRT, which is created from the certificate-based login from Azure AD.
Here’s a simple try which confirmed the successful creation of a PRT on Windows Server 2019:
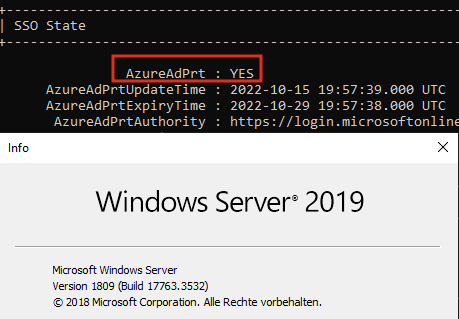
If you’re looking for a more user-interactive way, checkout Part2.
Configuration Azure AD
The configuration isn’t that complicated and there are step-by-step guides on MS Docs.
- You have to make sure to upload your at least one certification authority (CA) and any intermediate certification authorities in Azure Active Directory.
- The user must have access to a user certificate (issued from a trusted Public Key Infrastructure configured on the tenant) intended for client authentication to authenticate against Azure AD.
- Each CA should have a certificate revocation list (CRL) that can be referenced from internet-facing URLs, so Azure AD is able to perform CRL checking, otherwise the revocation of user certificates will not work and authentication will not be blocked.
- Configure the Certificate-based authentication Authentication method in your Azure Active Directory Security menu.
- Join your clients and your Citrix VDA’s into Azure AD or a hybrid environment (hybrid join).
After enabling certificate-based authentication, the new sign-in method appears and is selectable by users.
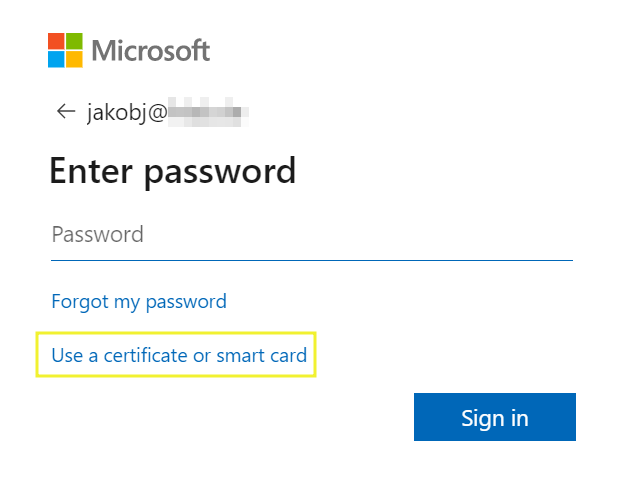
Configuration Citrix FAS
Long term short, there is no special configuration on Citrix FAS needed. Just configure your FAS servers as default, connect to your PKI and publish certificates for User logon.
Supported Platforms and Browsers
The following Windows platforms and browsers are currently supported. It’s only supported on Windows Hybrid or Azure AD Joined. Users also must be in managed domain or using Staged Rollout and can’t use federated authentication (ADFS) model.
- Latest preview build of Windows 11
- Windows 11 – after applying update kb5017383
- Windows 10 – after applying update kb5017379
- Windows Server 20H2 – after applying update kb5017380
- Windows Server 2022 – after applying update kb5017381
- Windows Server 2019 – after applying update kb5017379
- Microsoft Edge Browser
- Google Chrome Browser
- Apple Safari Browser
- Mozilla Firefox Browser
- Azure AD CBA supports both certificates on-device as well as external storage like security keys on Windows – which is a great way for BYOD
Hi, this seems to be interesting. Does the VM need any settings enabled, like allowing smart card logon?
It’s related on browser login, so the browser CBA / Smartcard Auth comes with the Azure AD Settings.
Configuration of FAS
Does the FAs rule need to be updated to use the CA in Azure?
Yes, you have to use the same CA on both sides.
If my O365 tenant is already federated with OKTA, can i still enable CBA for my Citrix VDI machines, which will use FAS cert for authentication?
If your domain is federated, there’s no Azure AD PRT, because federated Domains (with ADFS or Okta) will use Windows-Authentication silently to do SSO to M365 services. So you should have SSO to all M365 / Entra ID related applications by default.