Table of Contents
Overview
Another (and for the moment the last) Quickpost about getting a Primary Refresh Token (PRT) inside your HDX Session when using Citrix FAS combined with Entra ID Certificate-Based Authentication (CBA) which is my favorite solution when it comes to gaining SSO to M365 Apps inside User’s HDX Session.
I’ve choosen to write that quick summary because I’m getting different questions about my other FAS posts with pros and cons and I’m not sure if everyone is aware of the following simple solution.
To sum up (choose your needs):
- Using Entra ID CBA on the Clientside for getting a PRT – you need to enroll certificates on your (corporate) Devices
2. Using Entra ID CBA inside the HDX Session for gaining SSO to M365 Apps without a PRT – needs FAS allow in-session certuse
3. Using NetScaler without FAS for gaining SSO to M365 Apps with a PRT
4. This Post which should technically replace variant 2
Configuration
The config is pretty simple and there’s a great diagram showing the technical workflow. Thanks to Kerberos TGT, there’s no need for FAS allow in-session certuse:
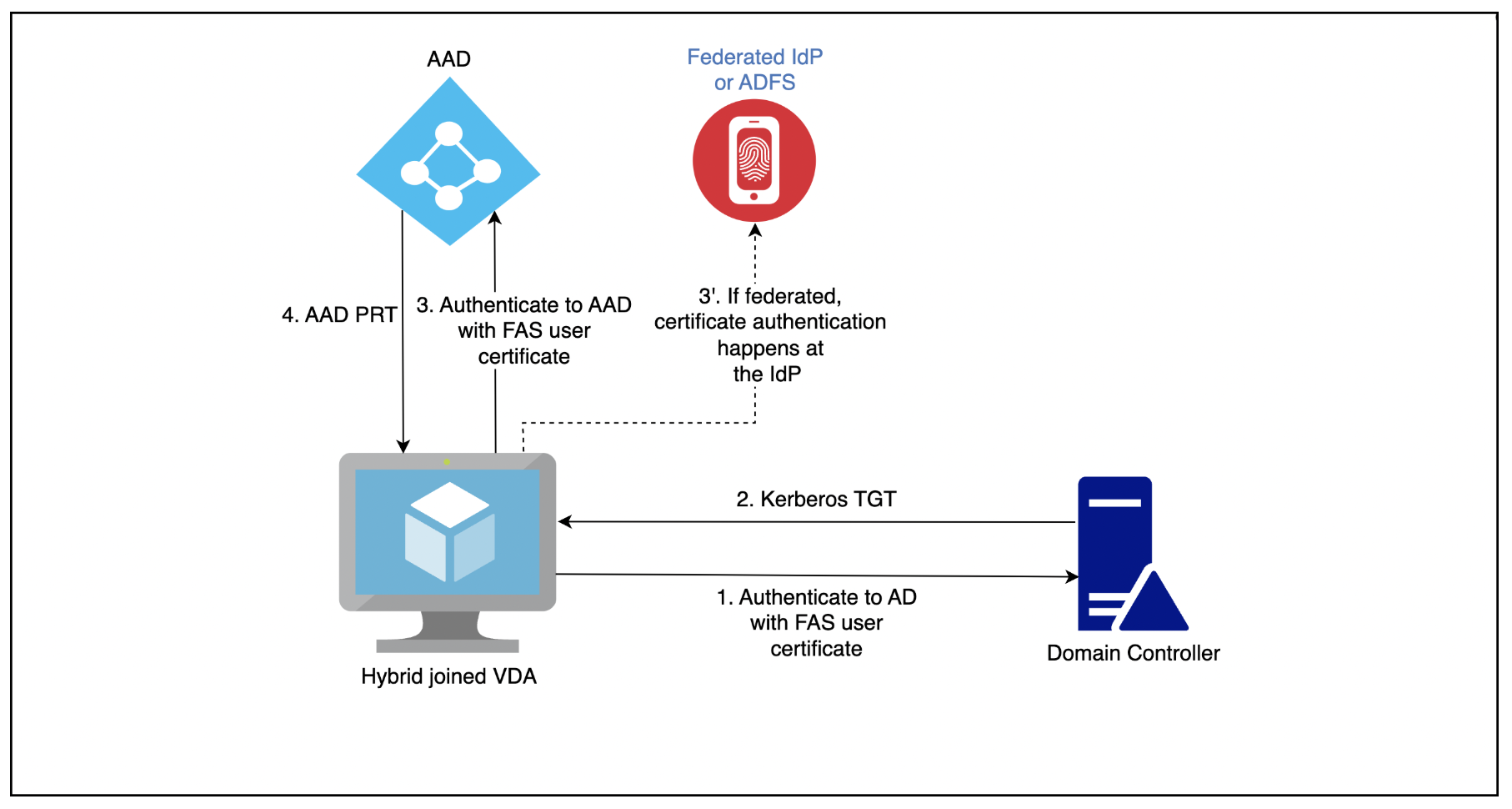
All four steps are happening during the Logon process of the User’s HDX Session to the VDA, which means in particular, the User doesn’t need access to the virtual Smartcard certificate from FAS. Not using in-session certuse is a great security achievement.
Requirements
- VDA is Entra ID hybrid joined
- Windows Server 2019 or later
- Windows 10 or later
- VDA has access to *.certauth.microsoftonline.com without any TLS Inspection
- Full CA-Chain is uploaded to Entra ID with (recommended, but not not absolutely necessary) publicly accessible Certificate Revocation List (CRL) URL
Entra ID CBA
Go to the Entra ID Portal and create your PKI – this is currently in Preview but will soon replace the classic Certificate authorities option:
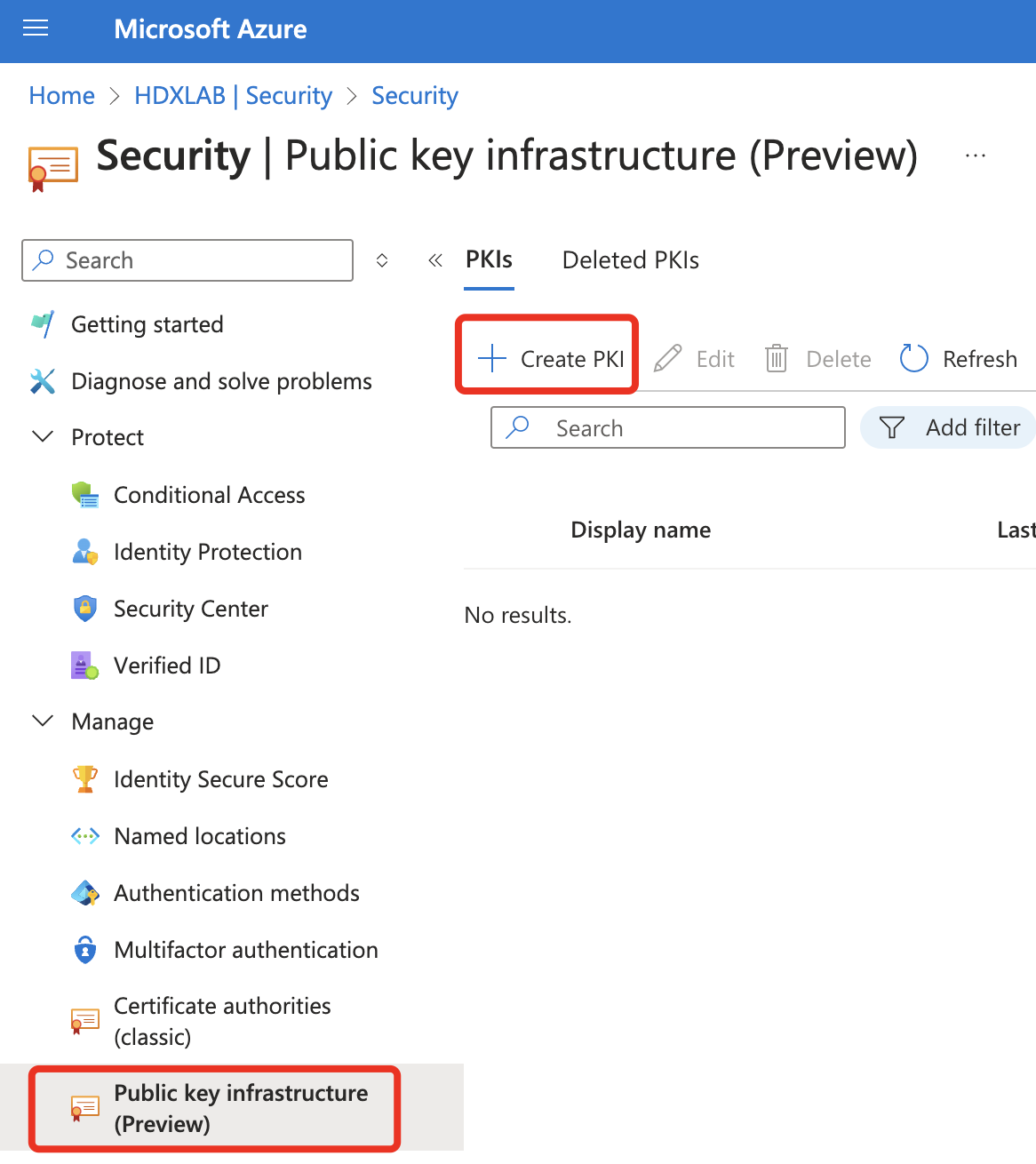
You can choose between entering a public URL (Upload CBA PKI) hosting your CA Certs or just uploading your CA Certfiles by manual (Add certificate authority):
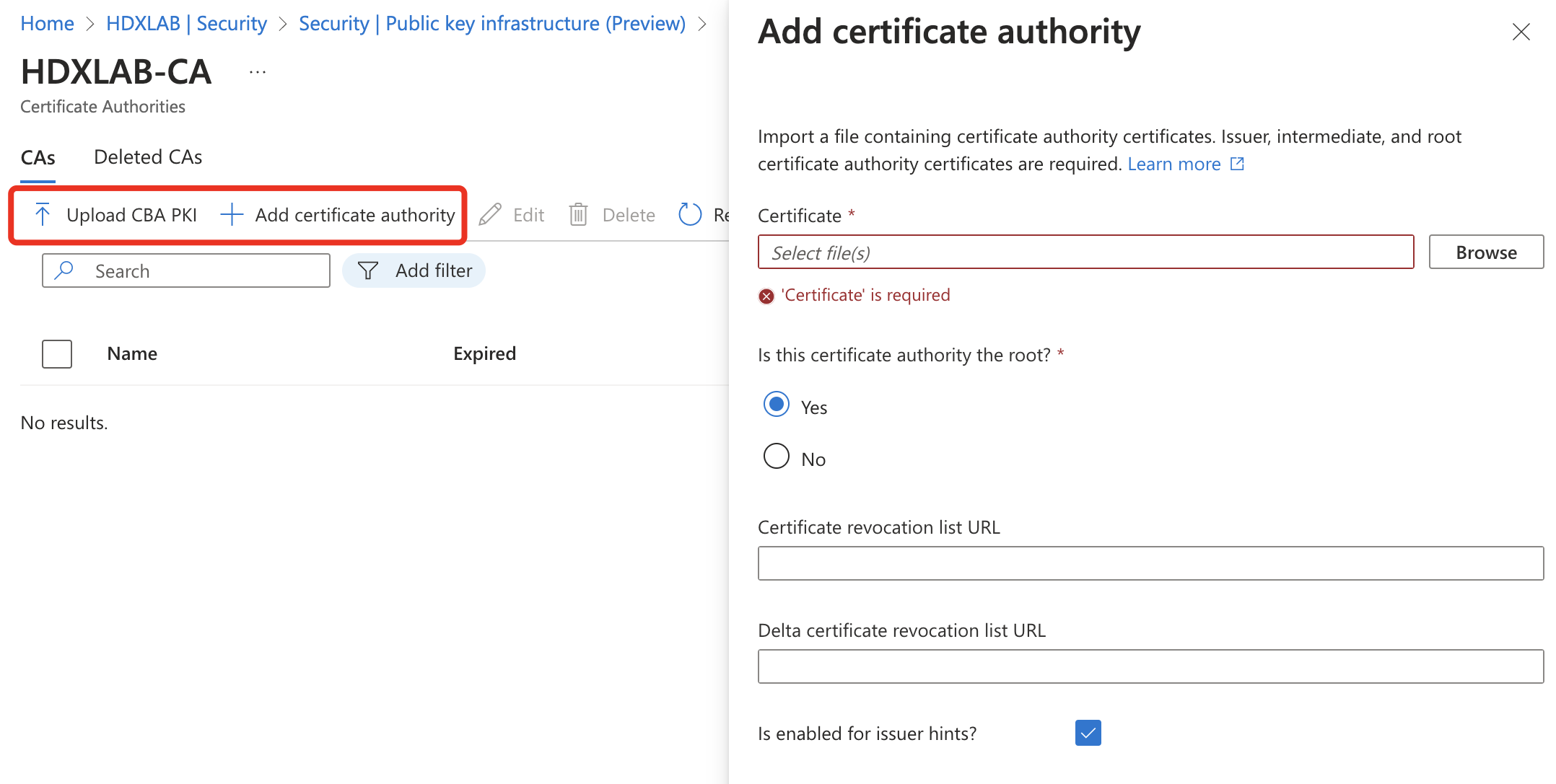
That’s it for the CA-Upload. Next is configuring and enabling the Certificate-based authentication Authentication method:
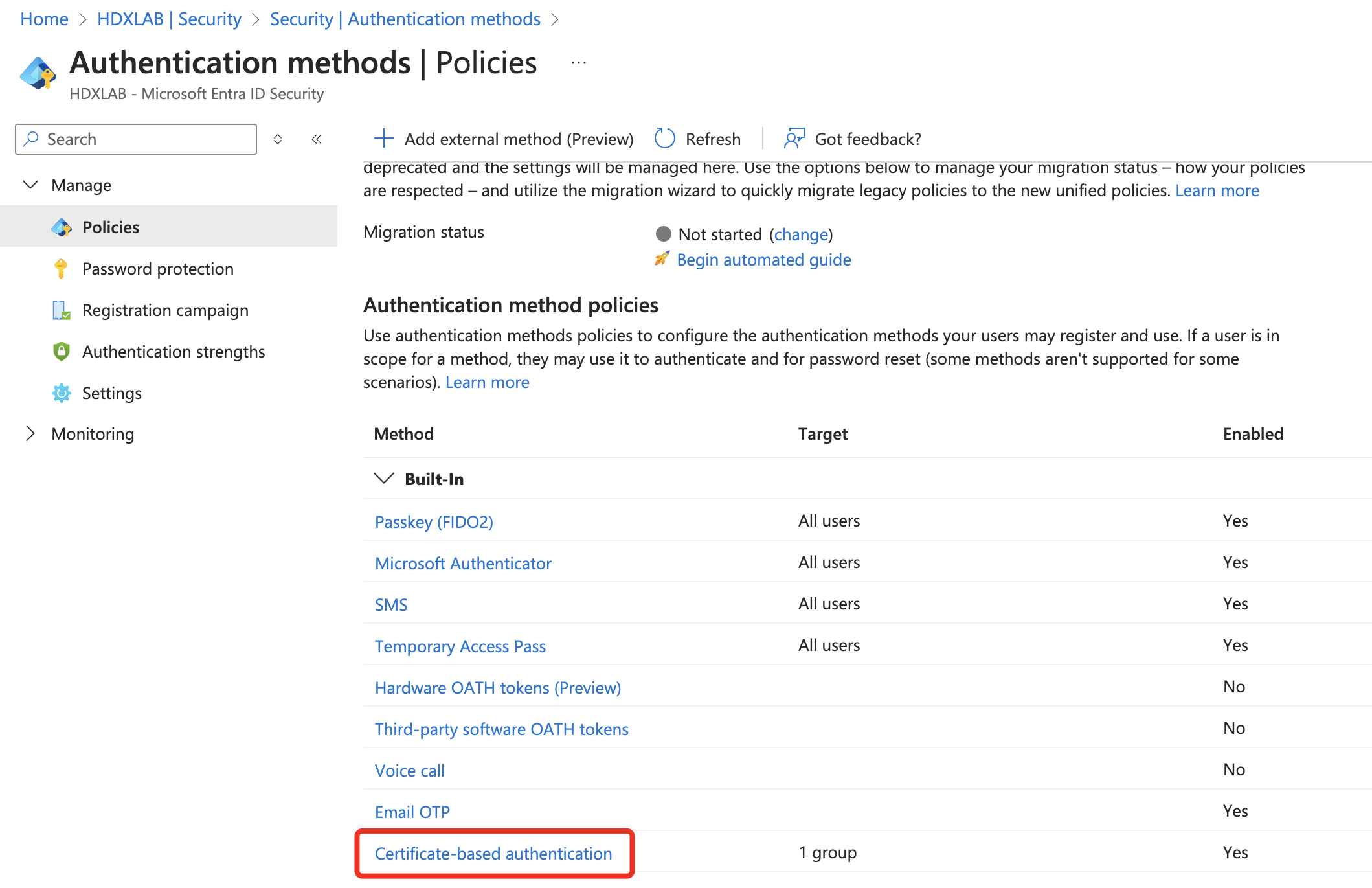
It makes sense to just enable it for a Usergroup which is using Citrix VAD / DaaS on a daily basis. You cannot filter on a device / machine group – which would makes sense to just enable CBA for all Citrix VDA’s. Technically you can select a device group, but it will never hit. Maybe this will come in near future.
The config part should look like this. Enable CRL validation only, when your CRL is public available. We will use Single-factor authentication as a Protection Level because we want silently logon to Entra ID without any User-interaction to get the PRT.
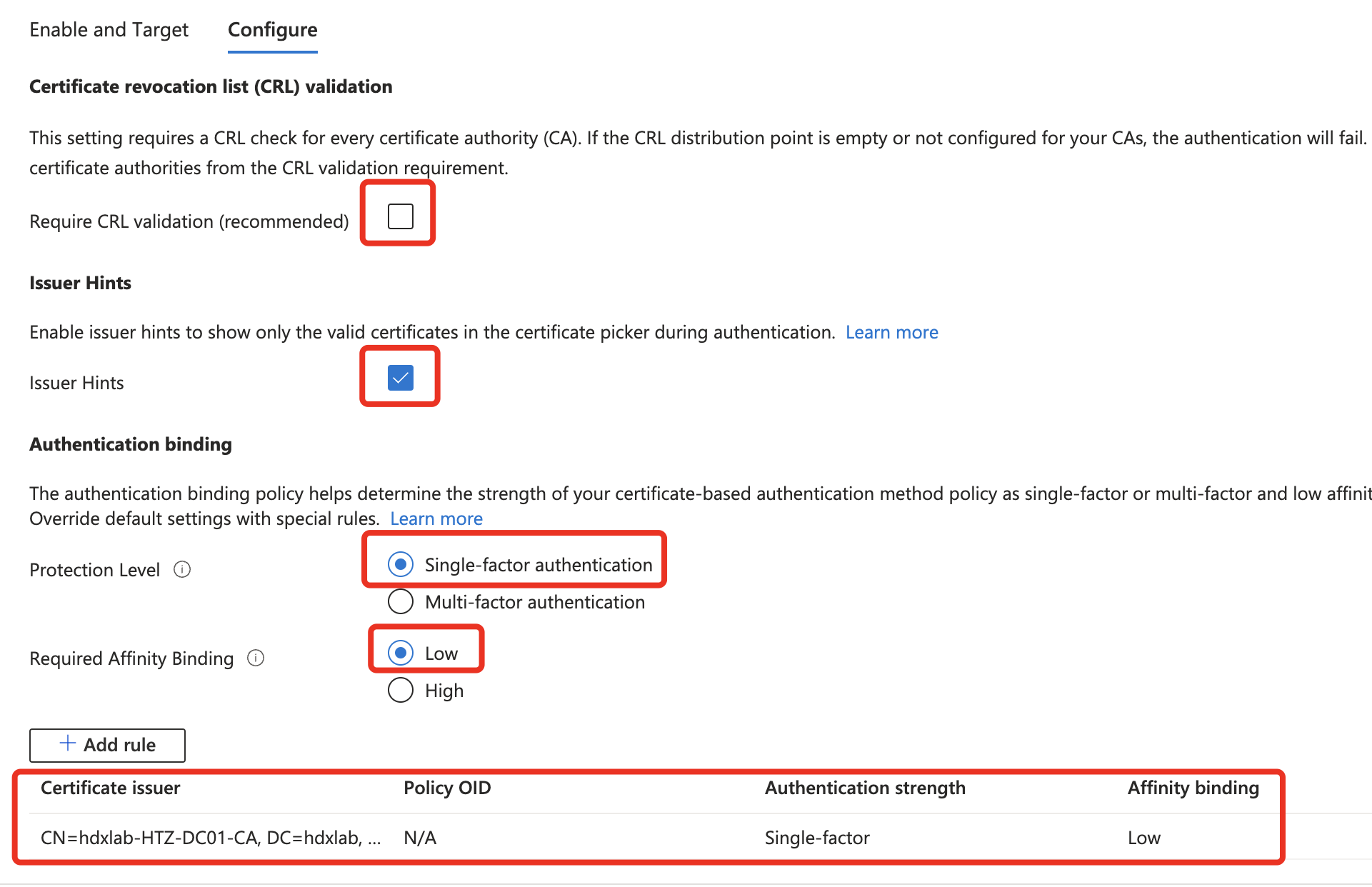
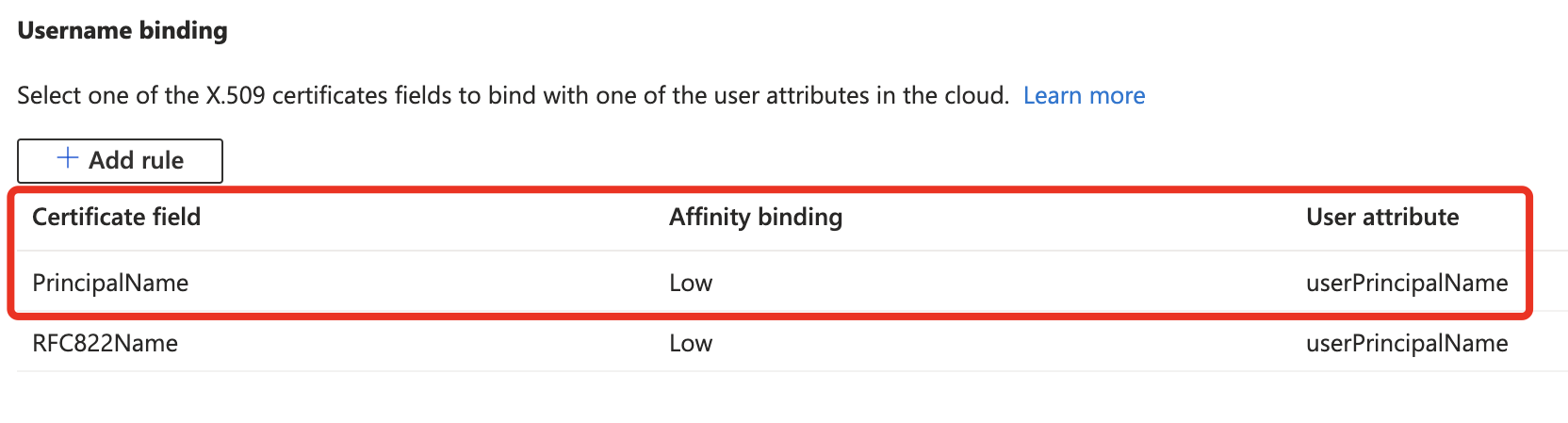
The minimum Ruleset should include the UPN-check, so the UPN of the user gets validated against the FAS Smartcard cert, where the UPN should be inserted:
That’s it. Just wait a few minutes to sync your settings into Entra ID, start your HDX session and validate the PRT.
When CBA is enabled for your User, but there’s no PRT inside your session – dsregcmd /status will give you some details why CBA failed (for example a not matching Certrule or a missing Intermediate-CA of your PKI)
Reset MFA / Register first MFA
At the moment, that variant is my preferred way for having stress-free SSO for all HDX Users. Adding some final notes here.
As soon as Entra ID CBA is enabled for all Users or a specific Group, Resetting MFA for a User isn’t working, anymore:
That’s because for Entra ID, CBA is also a MFA method. Two solutions for that. Remove the affected User of the Entra ID CBA-Group, Reset MFA, add the User, again.
Second option (which I prefer) is also solving another issue. When CBA is enabled for a User who hasn’t register any MFA-Method, yet and is trying to do that via aka.ms/mfasetup – a Certificate Validation failed auth-popup appears. Again, you can remove the User, register a preferred MFA-Method and add the User, again.
For that specific usecase, there is Temporary Access Pass (TAP). TAP is accepted by Entra ID for authenticating to the MySignIn (aka.ms/mfasetup) Page when there’s no other MFA-Method registered, yet. Just make sure TAP is enabled as Auth-Method in your Tenant.
Go to the affected User and create a TAP like here:
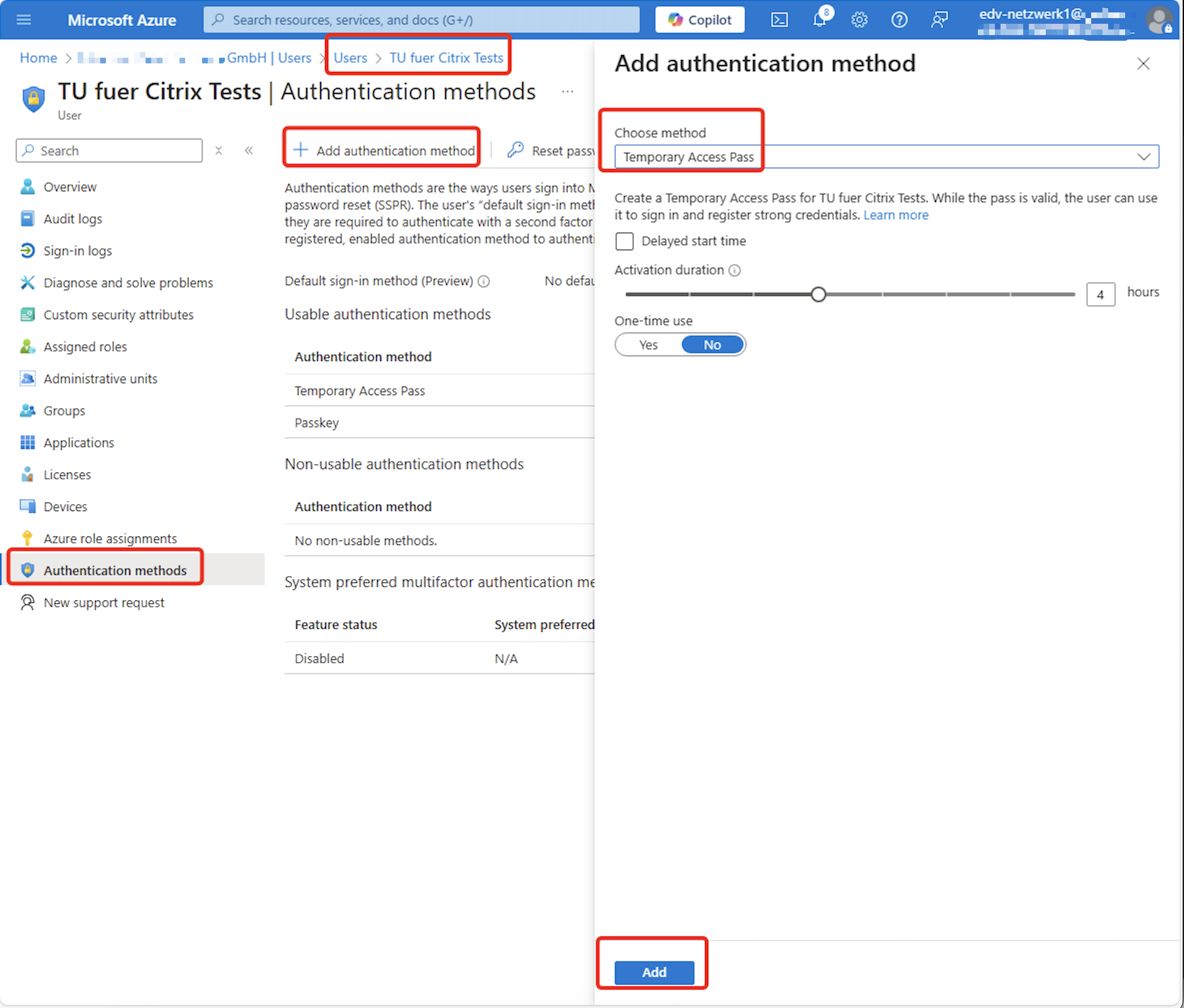
Wait a few Minutes, copy & paste the TAP to the User – as soon as the TAP is active (as said, wait a few minutes) the following Loginpage will appear to aka.ms/mfasetup (or aka.ms/mysecurityinfo)
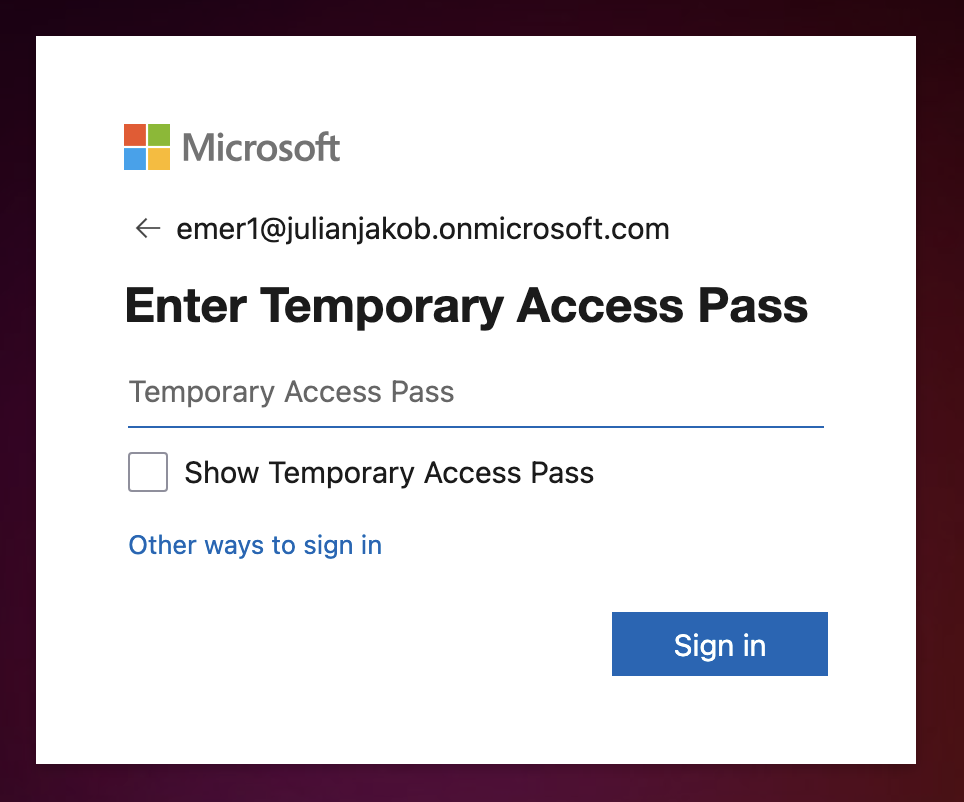
Use the TAP to authenticate and you are able to register a preferred MFA-Method or delete the (forgotten) MFA-Method and create a new one.
Regarding Security:
If the FAS smartcard cert of a user gets inside wrong hands – he’s able to logon to M365 / Entra ID as your identity. As the cert is not on the VDA level, make sure to use a separate Issuing-CA only for FAS and lockdown that CA and all FAS server’s. Think about using HSM, too.
Regarding Userexperience:
When enabling CBA for a user, there’s the smartcard logon-option showing up on all devices when the User’s logging on to M365 / Entra ID:
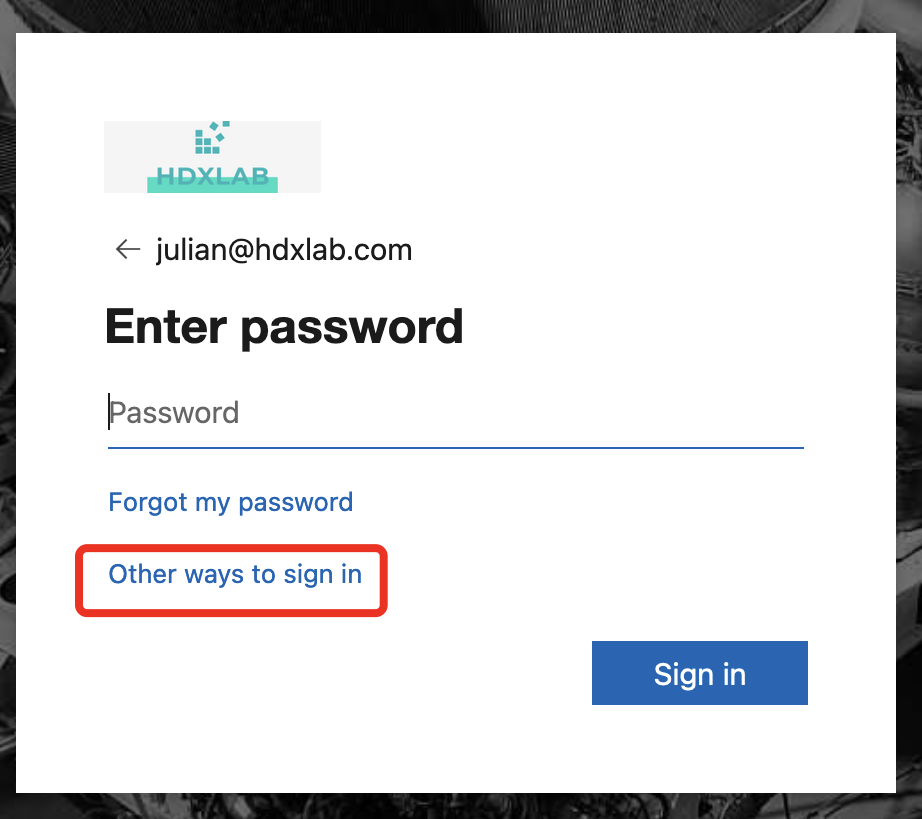
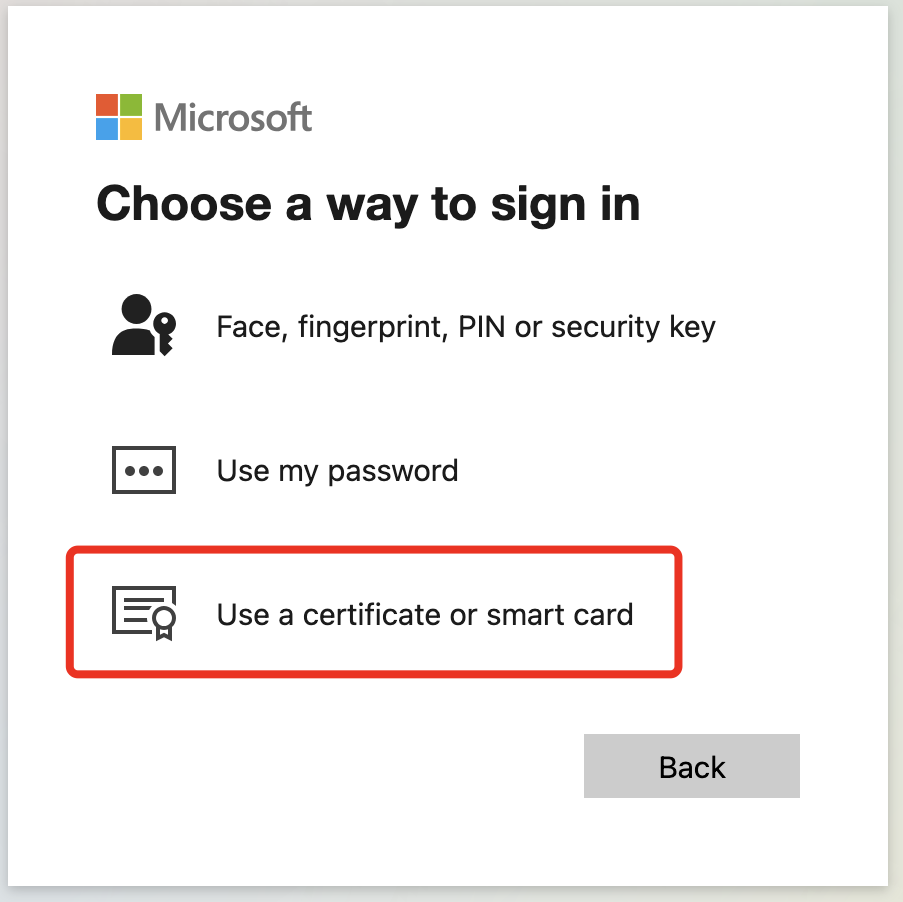
Which will fail, because there’s no matching cert on the clientside deployed:
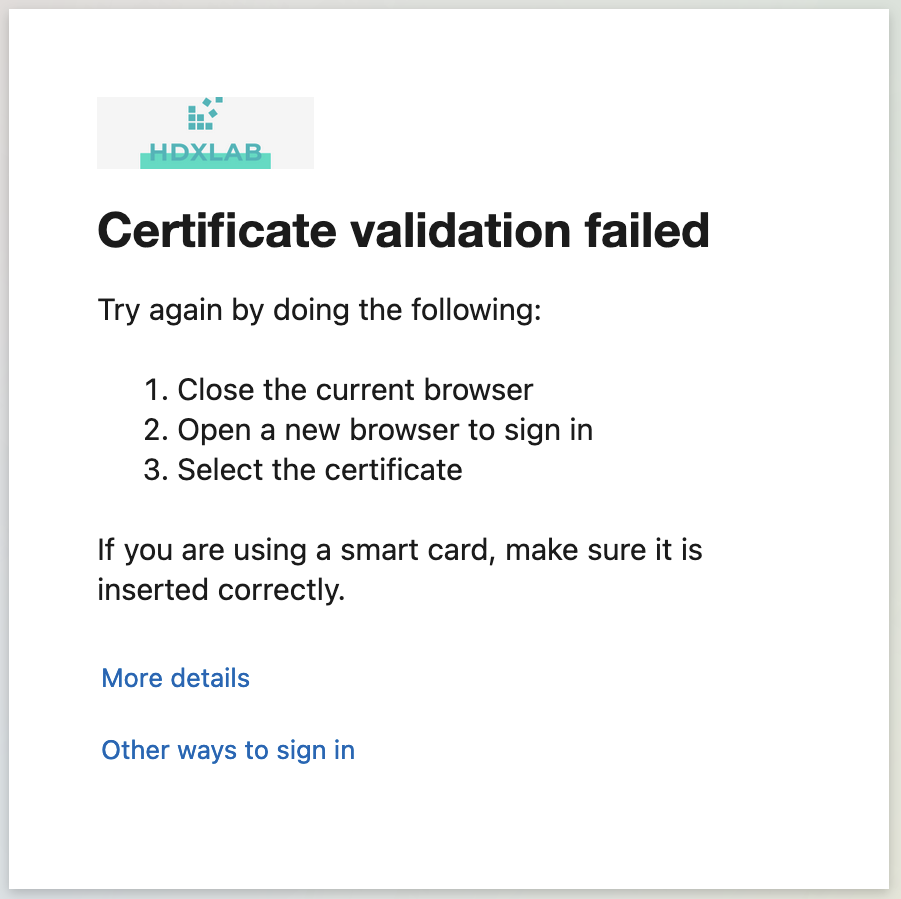
That could accidentally work when using the same Issuing CA for FAS and for Clientcerts (Eg Intune) with the User’s UPN, too. Make sure this can’t work.
Summary
Hopefully that Post answered some questions or misunderstandings for solving the missing PRT problems in a HDX world.
Hello! I have tried this config, I still experience Certificate Validation failed when configured to single-factor instead of multi-factor if I press the MFA Reset button
Hello Erik,
thanks for your details. I’ve updated the Post to write about the usage of TAP for that kind of issues.
Best Regards