Table of Contents
Overview
Recently a customer requested me to implement a Clientless VPN solution with Citrix NetScaler. CVPN? Wasn’t that the rewriting module which only works with simple Webapps and all other complex ones were failing or the rendering displayed buggy and incomplete?
Correct! But since 13.0, there’s a mode called Advanced Clientless VPN which replaces the legacy CVPN (CVPN V1) – I already wrote about that mode in context to HTML5 Workspace Sessions.
So let’s give it a try!
Configuration
NetScaler
Create a Session Profile and enable Clientless Access and Advanced Clientless VPN Mode in the Client Experience Tab:
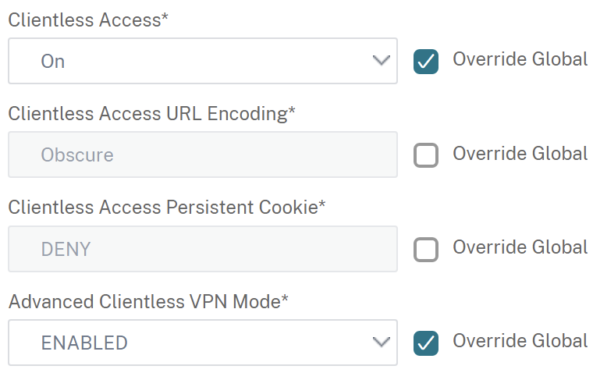
In Citrix Gateway -> Global Settings, add your internal Domain-FQDN to the allowed Domains for Clientless Access:
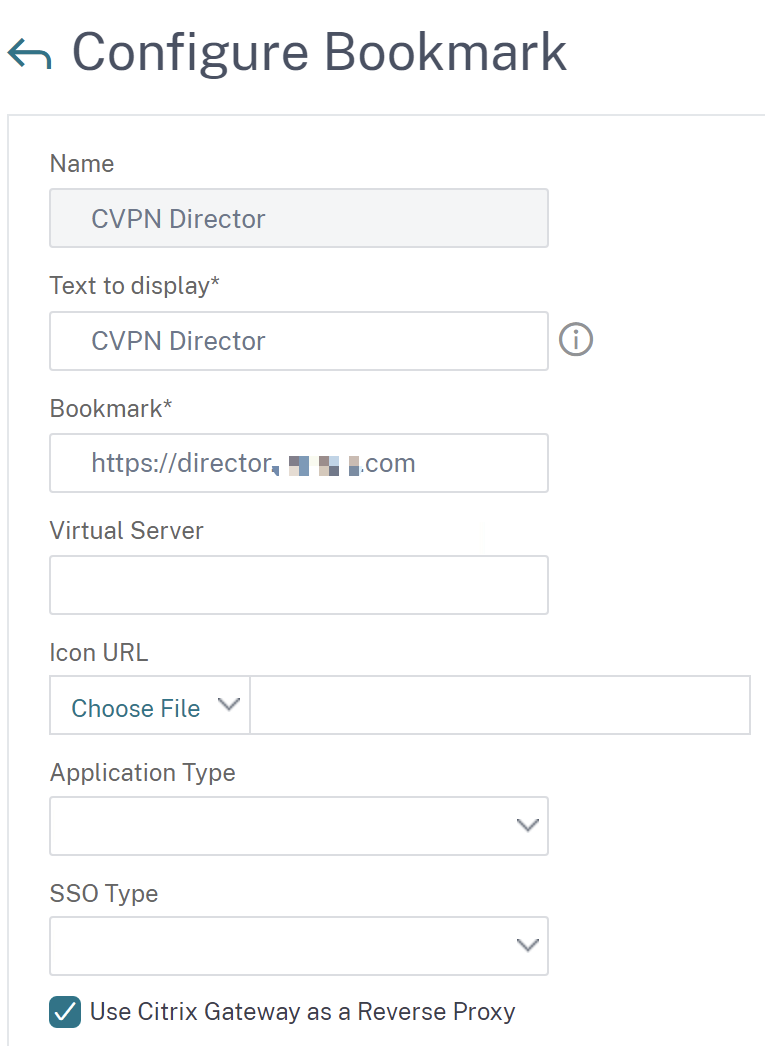
Create Bookmarks to your internal Webapps, make sure Use Citrix Gateway as a Reverse Proxy is enabled and bind these to your Citrix Gateway vServer (for everyone) or to AAA Groups for a filtering mechanism:
Certificate / DNS
The advanced clientless VPN rewrites URLs in a unique manner. This uniqueness is maintained for every URL per user. For example, if the web-application is hosted on https://webapp.customer.com, and the Citrix Gateway vServer is hosted on https://cvpn.customer.com, then the advanced clientless VPN rewrites it as https://cvpneqwerty.cvpn.customer.com. This means, every URL is rewritten as a subdomain of the Citrix Gateway vServer. In this new URL, cvpneqwerty can be decrypted back to https://webapp.customer.com.
Which changes are required to your SSL Certificate?
If you’re using a wildcard -> make sure *.cvpn.customer.com is entered as a SAN attribute, otherwise you have to get a new wildcard certificate
If you’re using a SAN -> make sure cvpn.customer.com and .cvpn.customer.com are entered as SAN attributes
DNS – to resolve URLs like https://cvpneqwerty.cvpn.customer.com to the same IP as your Citrix Gateway vServer, you must add a new record for your subdomain cvpn.customer.com called * with the same IP address or alternatively a record called *.cvpn.customer.com
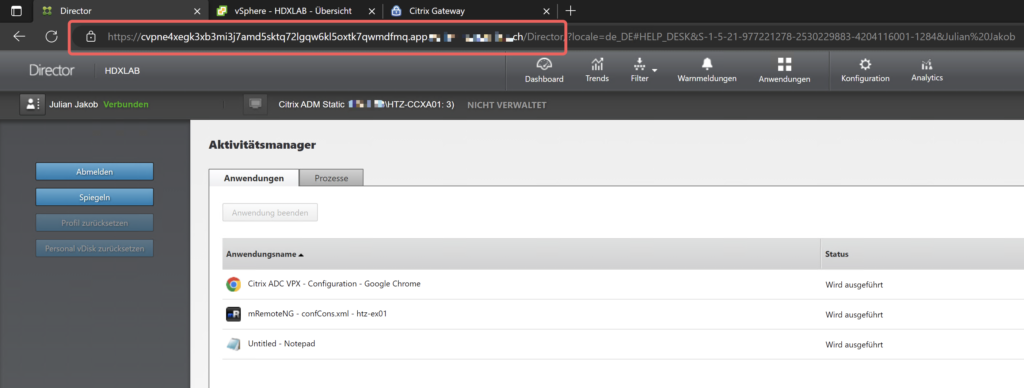
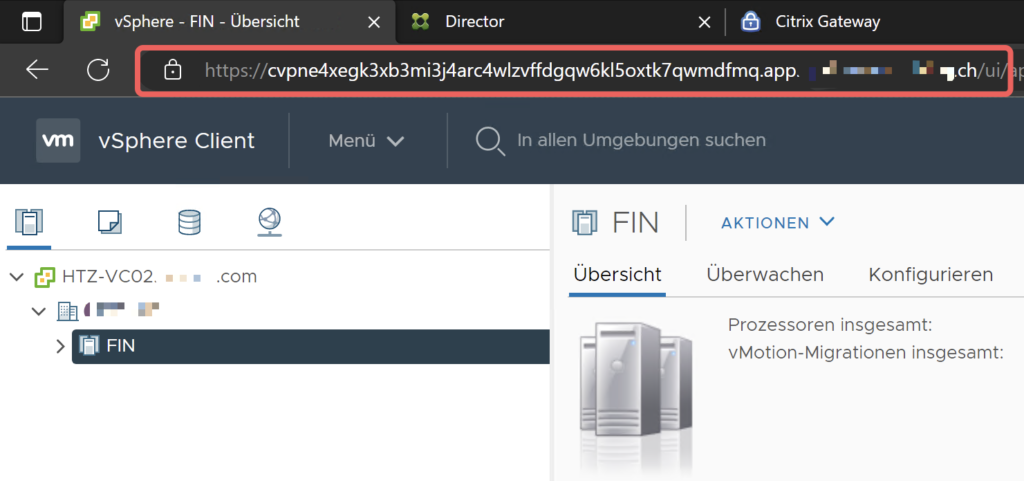
All done! These are some tests using advanced CVPN (My Citrix Gateway vServer is published as app.customer.com) to access a VMware vCenter or a Citrix Director, sure there are some limitations like the Shadowing Feature in Director or the VMware Web Console, as these are using CORS (Cross-Origin Resource Sharing) which isn’t technically supported by advanced CVPN. Microsoft’s Exchange OWA was also running out of the box.
Summary
To conclude, the Advanced Clientless VPN engine is really a great upgrade compared to V1, a simple way accessing Lab-Resources or just publishing internal Webapps for Users where there’s no need for Content Switching with AAA.
Hints
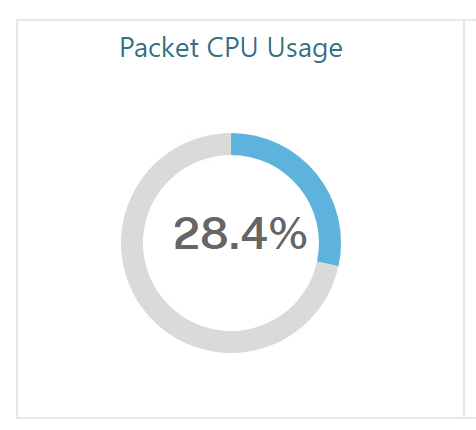
Depending on which kind of Webapps you are publishing with advanced CVPN (simple or complex) make sure you’re keeping an eye on NetScaler’s Packet CPU Usage. During my tests, the first VMware vCenter access, I noticed a high peak-usage, as there are many rewrites to process. Followed access by the same user (same browser) is handled by cache.

Hi Julian
thank you very much for the post, I have a question related to the Advanced Clientless VPN and Rewrite Policy, is there an expression in the policy to use that gives me the randomly generated DNS name of the Adv. Clientless VPN?
I tried with HTTP.REQ.Hostname but unfortunately it doesn’t work
Many thanks
Hi Reeno,
I think thats not possible, here’s what Citrix is saying:
“This uniqueness is maintained for every URL per user. For example, if the web-application is hosted on https://webapp.customer.com, and the VPN virtual server is hosted on https://vpn.customer.com, then the advanced clientless VPN rewrites it as https://cvpneqwerty.vpn.customer.com. This means, every URL is rewritten as a subdomain of the VPN virtual server. In this new URL, cvpneqwerty can be decrypted back to https://webapp.customer.com. The string cvpneqwerty is dynamic and therefore for SSL, you must bind the VPN virtual server with a wildcard certificate.”
In my environment, the cvpneqwerty string can change on the same Webapp after a relogin which makes it kind of impossible to filter.
Hi Julian,
did you put specified url on the vcenter bookmark ? I’m able to the go on the default webpage but when I click on login it try to redirect me on the url “https://vcenter.contoso.local/websso/SAML2/SSO/vsphere.local?SAMLRequest=” and failed
Thanks i
Hi Baptiste,
I only used the FQDN of my vCenter. Your URL looks like your vCenter is connected to an IdP to do SAML with? This will fail with cVPN, as the header get rewritten. Are you able to use a local / LDAPS Logonmethod?
Regards
Julian
Hi Julian,
thanks for your reply.
Well that’s the thing, I don’t use external identity with the vCenter, only the default local “domain” (vsphere.local).
In my lab the vCenter is in version 7.0U3. It’s seems to be the default behavior to redirect to the path /websso/SAML2/xxxxx to login.
Regards, Baptiste.