Table of Contents
Overview
Finally, with 14.1 Build 21.57 and 13.1 Build 53.17 there’s the long awaited support for using NetScaler’s Web Application Firewall (WAF) for all kind of Gateway vServer and AAA vServer.
This is a Quickpost about the configuration and some limitations.
Remember, this WAF functionality is free to use, including Standard, Advanced and Premium license. Use NS-Console Service or NS-Console (Minimum 14.1 Build 21.60) with unlimited vServer licenses for the optimal combination.
Configuration
WAF for Gateway / AAA is (at the moment) an integrated WAF solution which means, it’s NOT working as WAF for LoadBalancing / Content Switching. There are also no signatures to update, these are integrated in Firmware.
When Web Application Firewall protection is enabled, NetScaler leverages the built-in Web Application Firewall profiles ns-aaatm-default-appfw-profile, ns-aaa-default-appfw-profile, and ns-vpn-default-appfw-profile. The profiles contain the associated built-in API specification files ns-aaatm-spec, ns-aaa-spec, and ns-vpn-spec to ensure that network traffic is secure and compliant with the API specifications. – NetScaler Docs.
There’s also the current limitation, WAF is applicable to traffic in the default partition only.
As soon as you’re using one of the mentioned Firmware-Builds, there is a new option for WAF Protection.
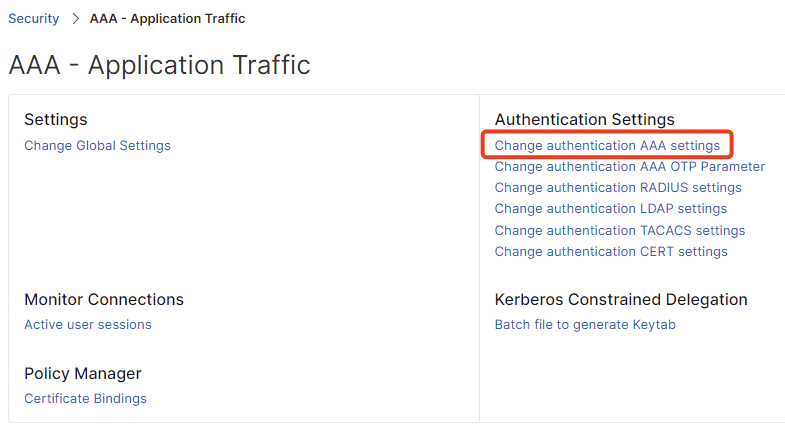
Go to AAA – Application Traffic and select the AAA settings.
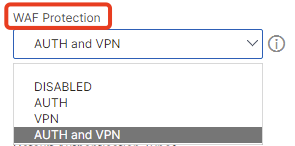
Per default WAF is disabled, you’re having four different options, choose your preferred one:
DISABLED – completely disable WAF
AUTH – enable WAF only for all AAA vServer
VPN – enable WAF only for all Gateway vServer
AUTH and VPN – enable WAF for all AAA and all Gateway vServer
That’s it – now WAF is enabled with default configured signatures provided by the NetScaler Team inside the Firmware.
Integration with NS-Console
As the WAF is enabled, now you would like to show your CISO how many blocks and higher protection your WAF is delivering, don’t you? 🙂
The easiest way is to integrate the WAF logs to NS-Console (previously ADM) so you don’t have to manually check the WAF-Logs on every NetScaler instance.
First step, again go to AAA – Application Traffic and select the AAA settings on your NetScaler.
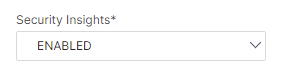
Enable the Security Insights option.
Now go to System – Profiles – Analytics Profiles. There’s now a builtin Security Insight Profile called ns-aaa-vpn-appfw-analytics-profile
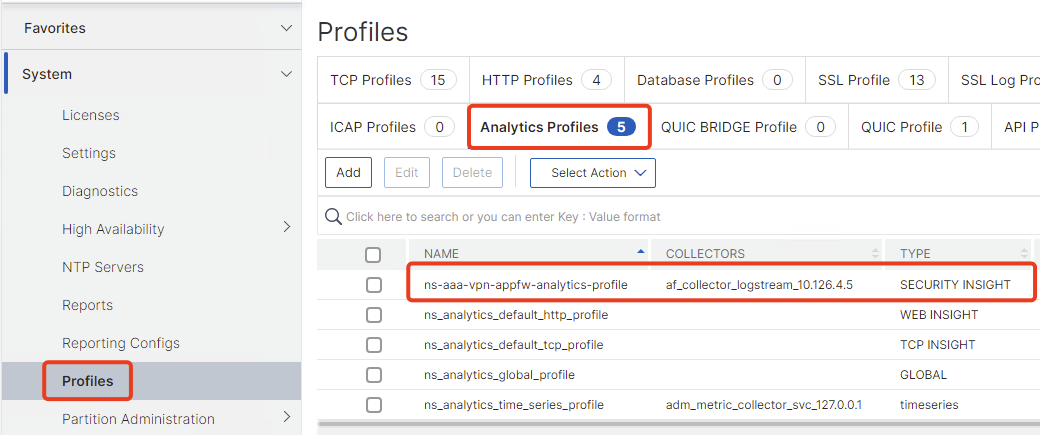
Select that Profile and bind your logstream collector of your NS-Console Appliance. If your NetScaler is configured with Gateway Insight or HDX Insight, you will find that logstream collector, because the collector is also used for these features, too.
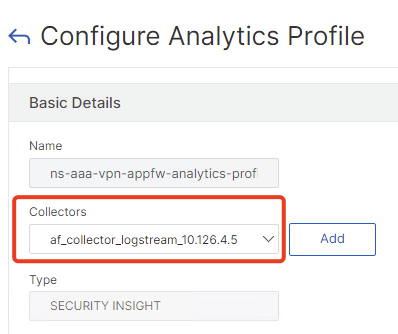
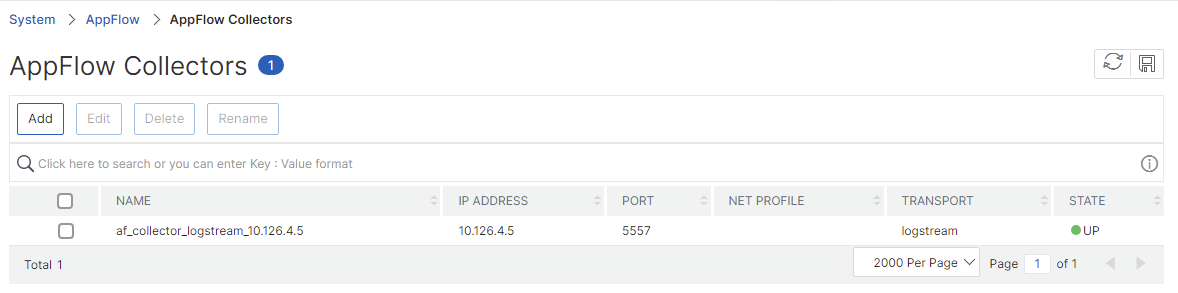
If there is no collector called “af_collector_logstream_xxx” – you an enable Gateway Insight and HDX Insight (which I highly recommend) – or you can create one manually here and make sure to use logstream with Port 5557 and the feature AppFlow is enabled:
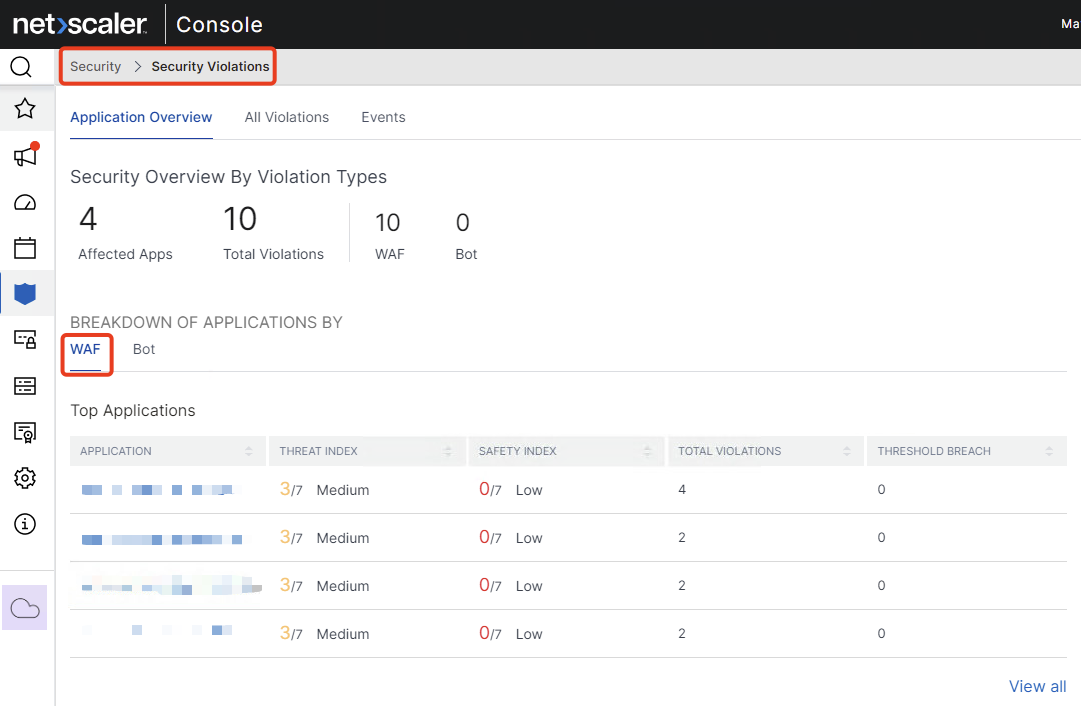
After a few minutes, go to your NS-Console and check the Security Violations Dashborad. Now there’s the category WAF and your AAA / Gateway vServer should be listed with first findings and blocks:
If you would like to doublecheck if the WAF is active, just browse to that simple URL of your Gateway / AAA vServer which will result in a block https://citrix.customer.com/?travelpayouts_redirect=https://oast.me
Also the WAF is blocking HTTP requests for example from ssllabs.com – you can check that on your ssllabs scan and will also find sth like that in the WAF blocks.
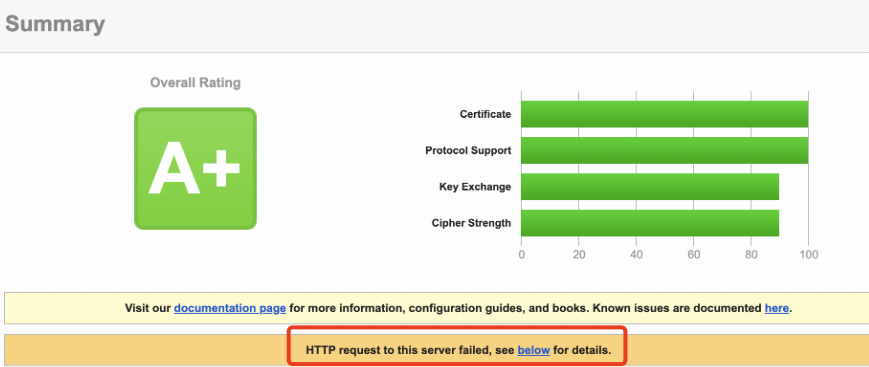
NS-Console WAF Log:
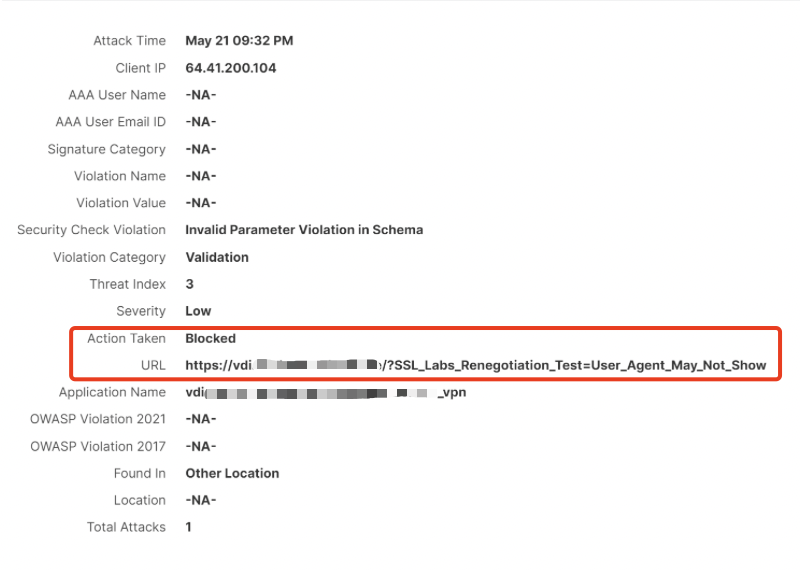
Summary
I think it’s a great start from NetScaler to integrate WAF for Gateway and AAA. A very big achievement would be to use the familiar WAF signatures to gain Hotpatching for future CVE’s which rely on the VPN / AAA engine.
Also make sure your NetScaler isn’t on CPU spikes before enabling WAF, because WAF will add some CPU consumption.
As this is the first build with that brandnew functionality, you can help NetScaler to improve that product – which means create a support case and send your WAF findings from NS-Console exported as CSV, in particular if you’re having some issues with false positives. Thank you.
You can also create a relaxation rule to bypass traffic – see details here
I would assume that the signatures update that NetScaler does on a regular basis would include updates to the signatures for AAA and VPN if needed. It will be interesting to see if this is the case.
https://docs.netscaler.com/en-us/citrix-adc/current-release/application-firewall/signatures
Thanks for the article Julian,
Will it work to attach a waf policy normally to a single GW server?
i want to only enable it for 1 Gateway, but i also want to utilize the waf profile for GW that citrix bulit.
I dont want to treat it using a normal waf profile.
Thanks again
Sadly not, it’s all related to the global AAA settings to enable or disable WAF.