Overview This Post contains informations about restricting the Usage of Citrix DaaS (Cloud Workspace customer.cloud.com) for limited Countries / Geo-Locations. In this scenario I’m using NetScaler as IdP of Citrix DaaS – so this is
Continue reading
It's all about EUC

Overview This Post contains informations about restricting the Usage of Citrix DaaS (Cloud Workspace customer.cloud.com) for limited Countries / Geo-Locations. In this scenario I’m using NetScaler as IdP of Citrix DaaS – so this is
Continue reading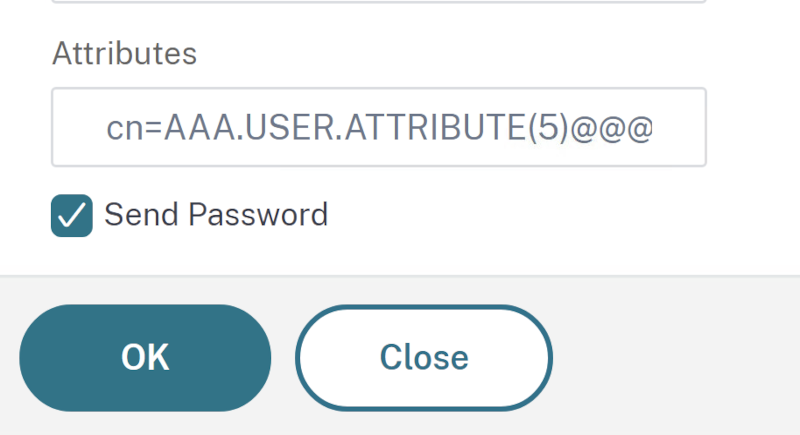
Overview Quick Post about a latest finding of an Issue when using NetScaler as OAuth IdP (doesn’t matter with which SP) and there is the need of sending some User-Attributes to the SP. Update –
Continue reading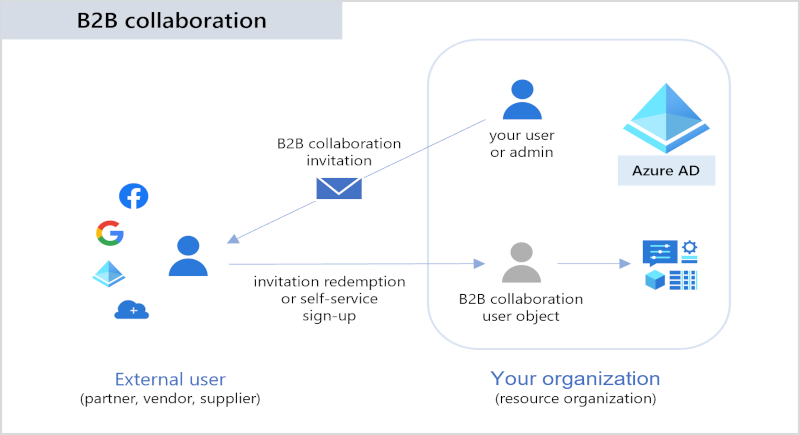
Overview Recently my namesake Julian wrote a great Post about choosing the correct Machine Identity in a Virtual Desktop Infrastructure – which is very important. This post will cover the other Hand – choosing the
Continue reading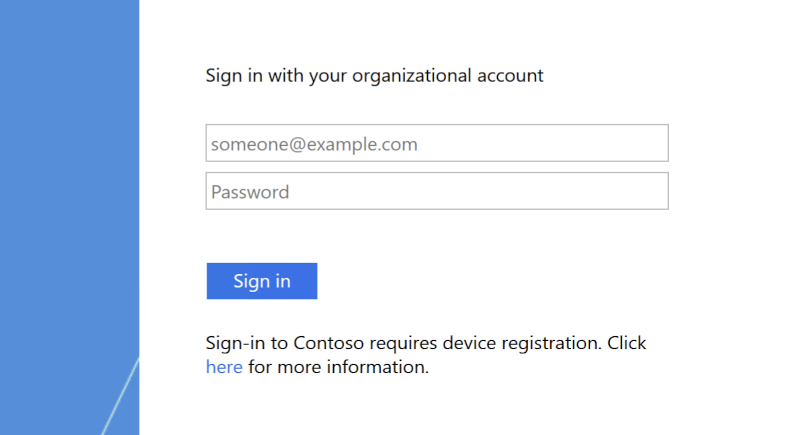
Overview This post will give you informations and the needed configuration for publishing a Microsoft ADFS (As it’s still not dead in the wild!) with NetScaler and using AAA for Authentication with SSO to the
Continue reading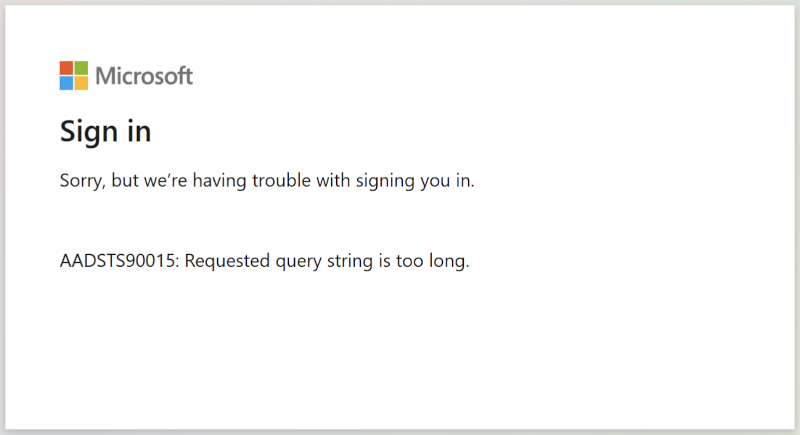
Overview This is a Quickpost about a desired architecture with Citrix DaaS, where a NetScaler is acting as OAuth IdP (DaaS Workspace Authentication is set to Citrix Gateway or Adaptive Authentication) and is acting as
Continue reading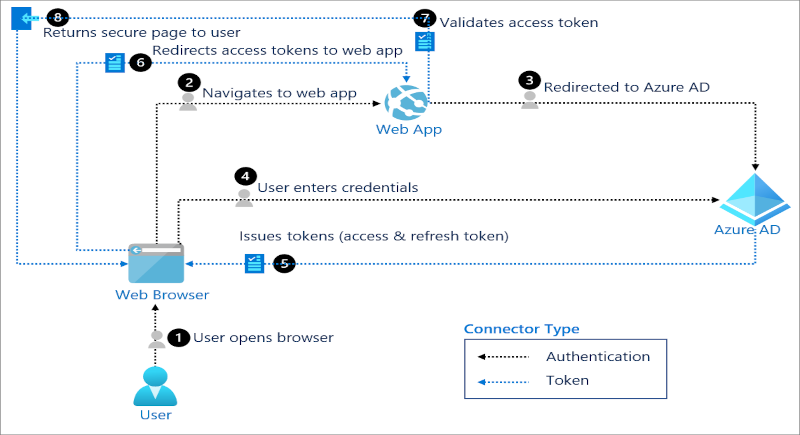
Overview What’s the biggest difference when choosing SAML instead of OAuth as the protocol when using Azure AD as IdP for NetScaler when it comes to User Experience (UX)? You should consider this Question when
Continue reading
Overview Recently I had the pleasure of being invited to the SwissCUGC Event in Zurich about the benefits for using Citrix ADC as an overall Identity Provider (IdP). It was really great fun and I
Continue reading
Overview Quick post about an OAuth-Issue with Citrix ADC’s SSL VPN. There is a missing hint in CTX225084 as this article is only refering to SharePoint deployments. OAuth can make use of the bearer authorization token. If users
Continue reading