Table of Contents
Overview
This is a Quickpost about a desired architecture with Citrix DaaS, where a NetScaler is acting as OAuth IdP (DaaS Workspace Authentication is set to Citrix Gateway or Adaptive Authentication) and is acting as OAuth SP to Azure AD simultaneously.
The goal is to use OnPrem AD group extraction first, followed by authentication to Azure AD, followed by redirect to Cloud Workspace. Why? Because the customer wants to go full with OAuth / OpenID Connect instead of SAML. It’s cert-renewal is easier and there’s the login_hint subject field support, which helps your users don’t have to enter their UPN more than one time.
Update 16.02.2024
NetScaler Engineering confirmed this issue should be fixed in the next 14.1 Build which is estimated to be released in April 2024. Same is also for the next 13.1 Build which will be released in May 2024.
Update 29.05.2024
I’ve tested the latest Builds and I can confirm, it’s NOT fixed, still getting the error. Reported back my findings and I hope the Engineering team is able to provide a final solution in the next months…
Issue
The setup isn’t that complicated. On the AAA vServer, there’s the OAuth IdP Policy for Citrix DaaS:
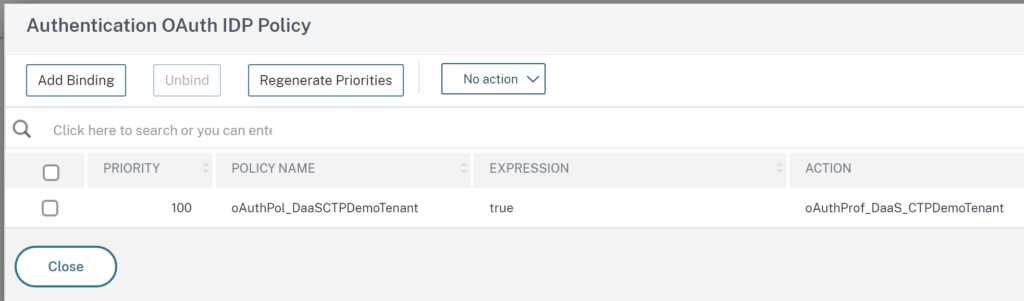
And there’s a no-auth group extraction LDAPS Policy followed by the OAuth SP Policy linked to Azure AD:
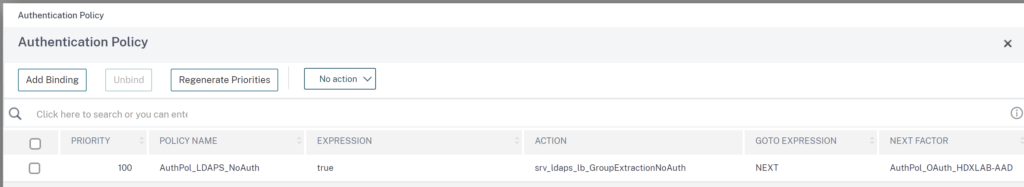
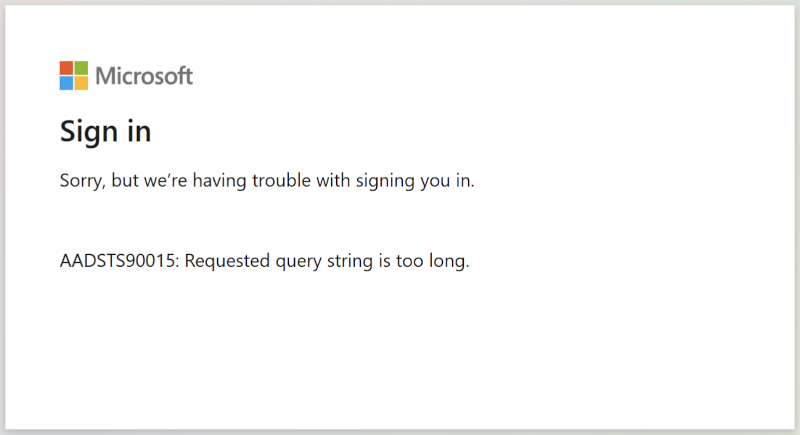
You may noticed the image of this post, containing the error message from Azure AD. Spoiler Alert! This configuration is currently not working. I’ve reported and traced the issue to Citrix Product Management and Engineering Team. They were able to reproduce the issue and raised an internal JIRA ticket NSAUTH-13209 for process tracking.
The state parameter in the request adds a lot of characters, to many for Azure AD, that’s why the error is shown. Removing the state parameter produces a successful authentication with Azure AD, but a failure on Cloud Workspace, as the missing state info contains required redirect uri informations.
To fix that, it will require a considerable code change in NetScaler and maybe some enhancement on Citrix’ Workspace Authentication Frontend – Athena.
Summary
As soon as I am able to publish a predictable estimated time of accomplishment, this Post gets updated. In the meantime you have to go with SAML for that scenario to work (But make sure to prevent a possible session takeover). Sorry!
Hi,
Did you have any update on this? I followed your Citrix NetScaler – OAuth to Azure AD with login_hint Subject Field but i’m now facing this error message.
Many thanks,
Amar
Hi Amar,
I know that NetScaler is working hard on that issue, I hope I can update my Post in about two weeks where there should be an update to that issue.
Stay tuned 🙂
Best Regards
Julian