Table of Contents
Overview
What’s better than having no MFA? A cost neutral (Assumed you’re using advanced license as a minimum) and easy to use MFA method where the Enduser hasn’t to deploy or register anything. Let’s checkout the Email OTP feature of NetScaler.
Configuration
There are some NetScaler Docs about Email OTP, mostly it’s mixed up with KBA registration for Self-service password reset (SSPR) or a minimum you have to register an alternate email address first.
In my configuration the Enduser hasn’t to deploy or register anything. Email OTP is ready to use as long as there is any Active Directory attribute configured with a valid Email address.
I’m using a nFactor flow to filter on a group, whereas member is getting the OTP via Email. If your not a member, the loginschema is switching to native OTP where the user has to register their device before the first usage. You can use your preferred filtering method.
Before jumping into the script, here’s how the flow is looking from the Enduser perspective when you’re member of the Email OTP group:
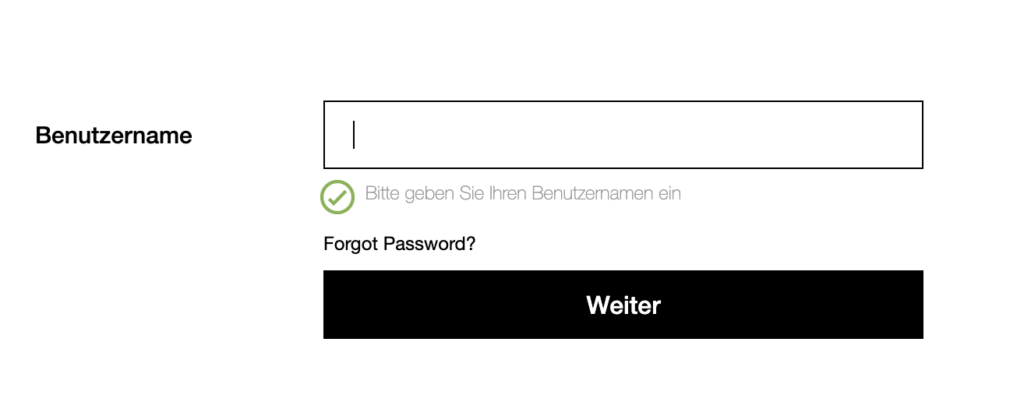
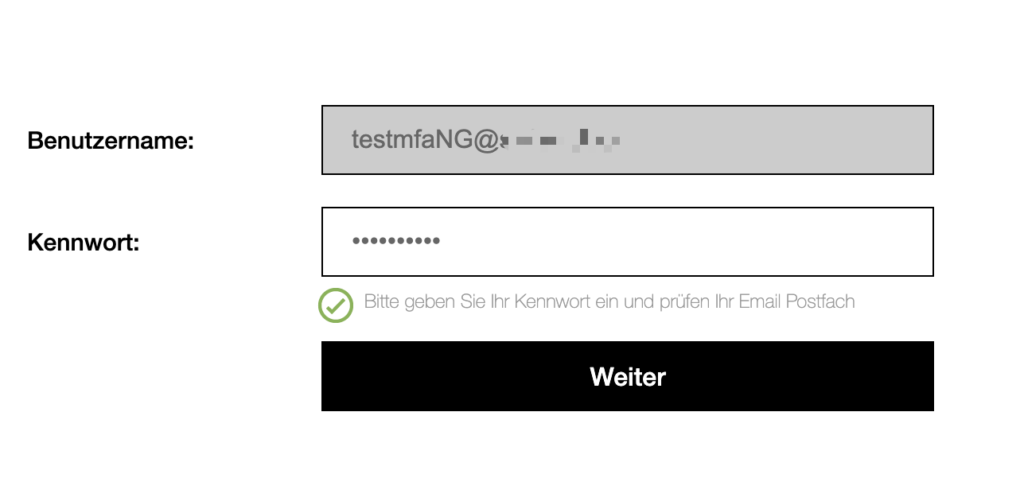
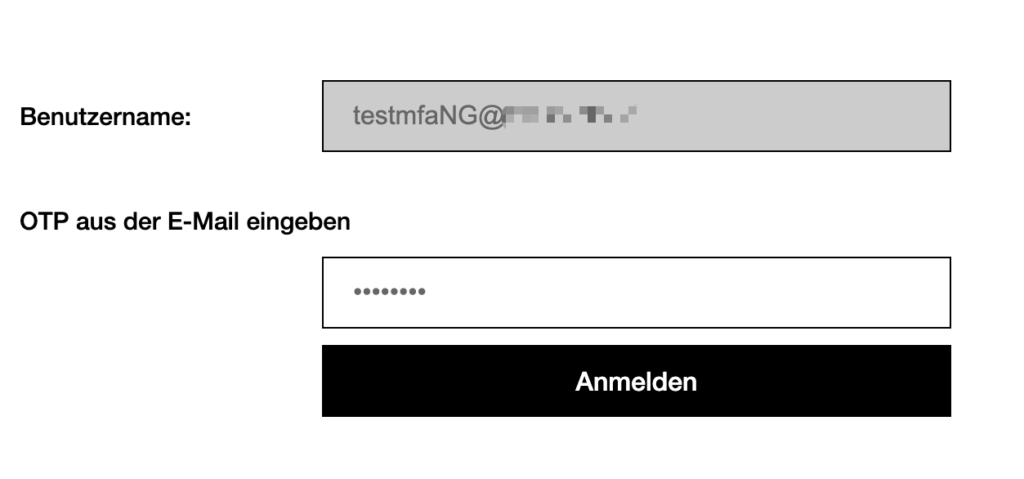
Here’s the nFactor configuration Script, one important thing to note:
- In the email action, I’ve configured the email Address to be inserted as alternate_mail attribute, the alternate_mail attribute is filled of the “mail” attribute from Active Directory, also seen in the LDAPS_GetEmailOTP ldap authentication action. You have to change these attributes if you would like to use other attributes.
#NetScaler Email OTP without any registration #First set Primary nFactor to Username only and filter to AD-Group whos getting Email OTP, otherwise User is getting native OTP add authentication emailAction AuthAct_EmailOTP -userName noreplyotp@contoso.local -password 12345 -serverURL "smtps://192.168.10.11:587" -content "OTP is $code" -emailAddress "aaa.user.attribute(\"alternate_mail\")" add authentication Policy Adv_Pol_EmailOTP -rule true -action AuthAct_EmailOTP add authentication policylabel email_Validation_factor bind authentication policylabel email_Validation_factor -policyName AuthPol_EmailOTP -priority 100 -gotoPriorityExpression NEXT add authentication ldapAction LDAPS_GetEmailOTP -serverIP 192.168.10.10 -serverPort 636 -ldapBase "DC=contoso,DC=local" -ldapBindDn serviceuser@contoso.local -ldapBindDnPassword 12345 -ldapLoginName userPrincipalName -groupAttrName memberOf -subAttributeName cn -secType SSL -passwdChange ENABLED -alternateEmailAttr mail add authentication Policy Adv_Pol_LDAPS_GetEmailOTP -rule true -action LDAPS_GetEmailOTP add authentication loginSchema Schema_NoLoginSchema -authenticationSchema noschema add authentication loginSchema Schema_OnlyUsername -authenticationSchema "/nsconfig/loginschema/customer/OnlyUsername.xml" add authentication loginSchema Schema_OnlyPassword -authenticationSchema "/nsconfig/loginschema/customer/OnlyPassword.xml" -passwordCredentialIndex 1 -SSOCredentials YES add authentication loginSchema Schema_EnterPasswordAndRADIUS -authenticationSchema "/nsconfig/loginschema/customer/DualAuth.xml" -passwordCredentialIndex 1 -SSOCredentials YES add authentication loginSchemaPolicy Schema_EnterUsername -rule true -action Schema_OnlyUsername add authentication loginSchemaPolicy Schema_OnlyPassword -rule true -action Schema_OnlyPassword add authentication Policy Adv_Pol_LDAPS_EmailOTP -rule "AAA.USER.IS_MEMBER_OF(\"ACL-OTP-Email\")" -action NO_AUTHN add authentication Policy Adv_Pol_LDAPS_NoAuth_GroupExtraction -rule true -action Auth_LDAPS_NoAuth add authentication Policy Adv_Pol_2FA -rule true -action NO_AUTHN bind authentication vserver AAA_vServer_nFactor -policy Schema_OnlyUsername -priority 100 -gotoPriorityExpression END bind authentication vserver AAA_vServer_nFactor -policy Adv_Pol_LDAPS_NoAuth_GroupExtraction -priority 100 -nextFactor GroupExtraction -gotoPriorityExpression NEXT add authentication policylabel LDAP_PasswordOnly_EmailOTP -loginSchema Schema_OnlyPassword bind authentication policylabel LDAP_PasswordOnly_EmailOTP -policyName Adv_Pol_LDAPS_GetEmailOTP -priority 100 -gotoPriorityExpression NEXT -nextFactor email_Validation_factor add authentication policylabel GroupExtraction -loginSchema LSCHEMA_INT bind authentication policylabel GroupExtraction -policyName Adv_Pol_LDAPS_EmailOTP -priority 100 -gotoPriorityExpression NEXT -nextFactor LDAP_PasswordOnly_EmailOTP bind authentication policylabel GroupExtraction -policyName Adv_Pol_2FA -priority 110 -gotoPriorityExpression NEXT -nextFactor Dual_OTP_2FA add authentication policylabel Dual_OTP_2FA -loginSchema Schema_EnterPasswordAndRADIUS add authentication policylabel NoSchema-2FA -loginSchema Schema_NoLoginSchema bind authentication policylabel Dual_OTP_2FA -policyName Adv_Pol_LDAPS -priority 100 -gotoPriorityExpression NEXT -nextFactor NoSchema-2FA bind authentication policylabel NoSchema-2FA -policyName Adv_Pol_Verify_OTP -priority 90 -gotoPriorityExpression NEXT add authentication policylabel email_Validation_factor -loginSchema LSCHEMA_INT bind authentication policylabel email_Validation_factor -policyName Adv_Pol_EmailOTP -priority 100 -gotoPriorityExpression END
Troubleshooting
Here are some tips for troubleshooting, for example there is no email been sent or you’re getting the well known NetScaler error Cannot complete your request.
Both NetScaler NSIP’s (Primary and Secondary) need access to your Mailhost via Port 25 (SMTP) or 587 (SMTPS).
You can find useful informations about the email process in the messages logfile in NetScaler, here’s an example for a non-working scenario, the Enduser is getting “Cannot complete your request” on the logon-process.
ThreadWorker_SendMailJob: [JobID: 10] Poco SMTP Mail Dispatch Failed. SMTP TYPE:2, SMTPException: Exception occurs. SMTP Exception: Login using LOGIN password failed: 535 Authentication failed. Restarting authentication process.
Make sure you’re getting a 250-AUTH LOGIN (Check basic authentication when using Microsoft Exchange) when telnet from NetScaler to your Mailhost and asking for ehlo yourmaildomain.
Summary
Fairly said, an email based OTP isn’t in todays security standards, as it’s quite simple spoofable. Anyway, it’s better than no MFA and for a limited period of use, it’s an easy to use feature without any registration input from the Enduser.
Great article, Julian!
A possible enhancement is to create a load balancer that NetScaler can use for the e-mail action. As such, the NetScaler would only require connectivity between the NSIP and the VIP address of the load balancer. I can imagine not everybody is willing to have outbound connectivity from an NSIP address.
Nevertheless, it is a great writeup!
Absolutely, great addition, thanks for that Jan!
Hello,
how forgot password works in this scenario?
Hi Julian
Do you think this could work with Adaptive Authentication in Citrix Cloud ?
I mean the 25 or 587 port toward an on prem smtp server ?
Hi Stephane,
docs is saying no https://docs.citrix.com/en-us/adaptive-authentication.html#additional-adaptive-authentication-capabilities and I think it will not work, due to missing forwarding config for the Cloud Connectors to your SMTP-Host.
that’s what I was thinking…
so the “solution” would be to integrate another vendor for the authentication who is able to send an email as second auth factor then
Anyone know of a way to change the Sender friendly name or subject of the email OTP.